Home » Industry Watch » The Technological
Mister Bill Gets Big 'Thank You' from Mother RussiaWindows users have no clue what dupes they are. But the Russians do.
Windows users have no clue what dupes they are. If they did they wouldn't be running Windows.
Windows users are the punks of the Internet. And they're being exploited in ways they can't even imagine. By one of the most sophisticated criminal organisations ever.
The Russian Business Network.
The Russian Business Network (RBN) are a semi-legit outfit in St Petersburg. They themselves don't do much illegal - their clients do. All the RBN do is give clients web presence and IPs.
The RBN aren't even an official registered limited company. They have no website. There's no way to contact them through traditional channels. If you want to do business with the RBN you have to reach them in the web underground - IRC for example. And the RBN don't take on clients hastily. To prove yourself worthy of RBN hosting you first have to prove you're engaged in criminal activity - not claim you are but prove you are.
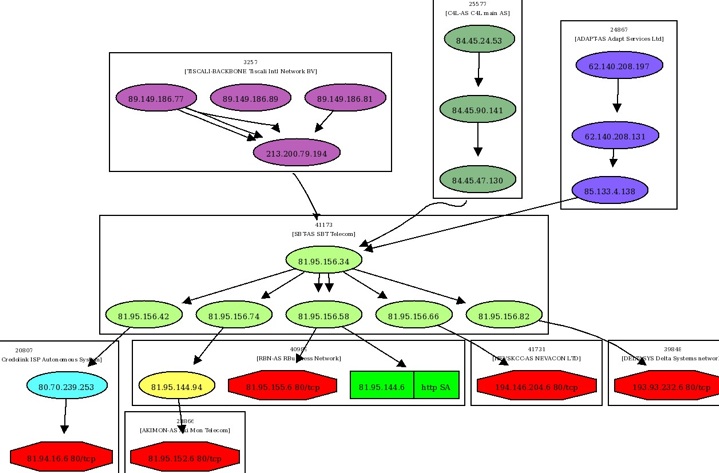
Upstream providers for the Russian Business Network. Of course none of this helps without the target Windows machines being such easy prey. |
And then for a lot more - about US$600 - than you'd pay elsewhere you get a web presence and all that implies. And $600 per client per month is a lot of money in Russia. But once you're set up on the RBN you can do literally almost anything. And the US$ come rolling back in. Lots of them.
The RBN and their clients are intensely patriotic: you never attack anyone in the home country. That could prove disastrous. An irate Windows user in Russia might file a formal police complaint - and that could interrupt the normal flow of revenue. Much more prudent to attack Windows PC suckers in the US, today the most formidable concentration of web suckers in the world.
role: RBusiness Network Registry
address: RBusiness Network
address: The Century Tower Building
address: Ricardo J. Alfari Avenue
address: Panama City
address: Republic of Panama
phone: +1 401 369 8152
remarks: Points of contact for RBusiness Network Operations
remarks: ------------------------------------------------------
remarks: Routing and peering issues: noc@rbnnetwork.com
remarks: SPAM and Network security issues: abuse@rbnnetwork.com
remarks: Customer support: support@rbnnetwork.com
remarks: General information: info@rbnnetwork.com
remarks: ------------------------------------------------------
e-mail: noc@rbnnetwork.com
admin-c: JK4668-RIPE
tech-c: JI424-RIPE
nic-hdl: RNR4-RIPE
mnt-by: RBN-MNT
source: RIPE # Filtered
person: John Kerch
address: Republic of Panama
e-mail: ripe@rbnnetwork.com
phone: +1 401 369 8152
nic-hdl: JK4668-RIPE
mnt-by: RBN-MNT
source: RIPE # Filtered
person: Joseph Igopolo
address: Republic of Panama
e-mail: support@rbnnetwork.com
phone: +1 401 369 8152
nic-hdl: JI424-RIPE
mnt-by: RBN-MNT
source: RIPE # Filtered |
The Russian Business Network are registered in Panama City. They control the IP ranges 81.95.144.0 - 81.95.147.255 and 81.95.148.0 - 81.95.151.255. |
Both Mpack and Storm are run from the RBN. So are dozens of other superworms. The botnets controlled by RBN clients are of Armageddon proportions.
Some legit ISPs have taken to blocking the RBN IP range as no benign traffic ever emanates from there. But that doesn't stop the Russians: today it's dead easy to use compromised Windows PCs in the US and elsewhere as proxy servers so the ISP networks don't see where the traffic is really coming from.
These activities aren't pranks - this isn't a question of uncontrolled worm outbreaks such as ILOVEYOU or AnnaK. These are sophisticated focused merciless attacks on selected networks and corporations.

The Windows PCs are used not only to spread the worms but to gather data (keystroke logs etc) and recruit further clueless Windows PCs into the botnets. Once in the botnets the PCs are even used to begin electronic fund transfers back ultimately to the clients in Mother Russia.
And the clueless Windows user sits there, fires up XP or V*STA, checks for antivirus updates, goes surfing - and all the while all that's noticed (if at all) is that the Acer/Dell/HP seems to be going a bit slower than it did those first few minutes online months ago when the box first arrived.
So Mister Bill gets a big 'thank you' from Mother Russia: crime has never been able to flourish like this. With Windows and Mister Bill's third rate crapware prevalent amongst the clueless RBN clients don't even break into a sweat.
Think about it next time someone asks you if you'd support Bill Gates as 'man of the year'.
Microsoft® Windows® is a registered trademark of Microsoft Corporation: Be stupid. Contribute to crime. Use Windows.
See Also
Security Fix: Mapping the Russian Business Network
Security Fix: Taking on the Russian Business Network
Washington Post: Shadowy Russian Firm Seen as Conduit for Cybercrime
|