Home » Industry Watch » The Technological
They Think It's OKReflections on Wsnpoem and other typical Windows disasters.
Windows users simply don't get it: no one has to jump through so many hoops, pull out so much hair, and waste so much time in the hopeless struggle to say secure, prevent hijacks, prevent loss of identity, bank balances, data corruption. No one else. Yet they don't see this. They can't. There's no way anyone in their right mind puts up with such nonsense if they have a clue.
Looking back over the disaster that's the Wsnpoem hijack is physically nauseating. There are so many hidden gems in those endless lines of gibberish that otherwise go unmentioned.
- 'I have run both spybot and ad-aware, both programs report it but are unable to remove it...' Those two are the leading anti-spyware products on the market. If they can't reliably get rid of spyware then who can?
- 'C:\PROGRA~1\Grisoft\AVG7\avgamsvr.exe'. The dude's got Grisoft antivirus running too.
[And Microsoft are still using pre-Windows 95 mangled paths 14 years on.] Nothing helps.
- 'C:\Program Files\internet explorer\iexplore.exe'. This dude wants to be secure but he's still running Internet Explorer.
- He's got SO MUCH JUNK tossed onto that box: Yahoo Toolbar; PC Guard (which doesn't seem to help either); Google Toolbar; Google Toolbar Notifier; 'Athens Toolbar'; Office 11 and assorted Office 11 crap; Windows Messenger; 'Office Genuine Advantage Validation Tool' [haha]; 'Windows Genuine Advantage Validation Tool [oh barf]; PCPitstop Utility; EMSI Software a-squared Anti Malware [which didn't help either]; Lycos Mail crap; craploads of ActiveX controls; Google Updater Service; and two separate defraggers. So there are not two but SIX (6) antivirus/anti-spyware systems on that box. SIX.
And yet nothing helps. Nothing. He's come with his cap in hand to the website of the one of those spyware killers instead.
- 'You have a password stealing trojan. Do not change any of your passwords using this machine until it is clean. You need to take precautions for any banking, credit cards etc that you may have used with this machine.'
Seriously: when's the last time anyone on a Unix system had to deal with something like this?
- Through the laborious process that follows two more anti-spyware products are added to the mix: SUPERAntiSpyware ('removes ALL the spyware not just the easy ones'); and SpywareBlaster ['the most powerful protection program available - keep your system spyware-free and secure'].
- 'Disconnect from the internet. If you are on Cable or DSL unplug your computer from the modem.'
Absolutely totally amazing. Why would anyone put up with this - if not for the belief everyone went through this same thing all the time? How is it possible to keep people so in the dark?
And the jungle of anti-spyware utilities all promising they won't prove inadequate as all the others have - and yet at the end of the day not a one of them is adequate anyway. It's all hype. How is a punter to figure out what to do? Figure out which of these obscenely innumerable AV clones actually works?
Talk to a neighbour? 'Oh I used Kick-Em-Out™ a few years back and it was really good!' Oh yeah?
And what about online banking? And the PC Pit Stop d00dette said 'don't change your passwords, contact your bank' and all that. Hello? These PCs are to be used for computing - for financial transactions? There wasn't any danger before the PC came along, was there?
System administrators don't worry about any of this anymore. Someone got a Windows box went pear shaped again? Take the box away, give the punter a new one, put the old one in storage and recycle it - wipe and reinstall. And prevent your users from storing anything locally.
But kitchen table users can't do the same thing. Kitchen table users have to come to PC Pit Stop and get help - when the hundreds (thousands) they've wasted on anti-spyware that promises everything but delivers nothing fails yet again.
But hey - can't they wipe and reinstall? This is what's happened to the Windows market since you got out: resellers don't include install media anymore. Great, innit? So you can't wipe and reinstall anyway even if you want to.
One can almost smell the stench of conspiracy.
BREAKING NEWS
Of late there's been a novel exploit running rampant on Windows computers. Brian Krebs gave it some attention a fortnight ago. The tack uses hilarious subject lines to lure people; they all start with 'msnbc.com - BREAKING NEWS'.
Iran Kicks America in the Nuts
Illegal Immigrants Seize Control of the US
Paul McCartney Gets Back with Heather Shock
Release of Nancy Pelosi Sex DVD Causes Mass Erectile Dysfunction in US
Taking the bait one is met with the following.
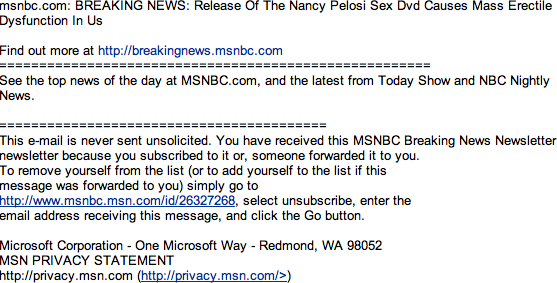
The link always pretends to be to http://breakingnews.msnbc.com - which is a legitimate URL. The URL you arrive at is of course anything but. It looks like a phishing site but there's the lure of watching a video clip - except of course you need a codec. Good luck for you: you can download it right away.
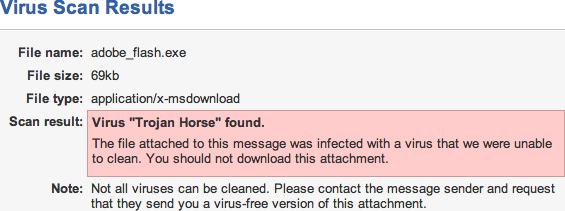
And of course it's yet another hack no one can get rid of. [Breaking out in a Cold Windows Sweat™ again?]
But that's not where the story lies. Not this time. The story lies in how this particular attack propagated.
msn_video.html
By some method still unknown this particular hack has been able to break into otherwise legitimate websites, put up the fake MSNBC page 'msn_video.html' - and even install the MSNBC 'favicon.ico'.

This site has been in contact with some of the victims; in some cases actions have already been taken; but this is an automated hack and the cure is not going around and contacting people.
And how can a hack like this have been possible? Could it have been this?
HTTP/1.1 200 OK
Content-Length: 15704
Content-Type: text/html
Server: Microsoft-IIS/6.0
X-Powered-By: ASP.NET
MicrosoftOfficeWebServer: 5.0_Pub
Connection: close
HTTP/1.1 200 OK
Content-Length: 15704
Content-Type: text/html
Last-Modified: Sat, 16 Aug 2008 12:34:16 GMT
Accept-Ranges: bytes
Server: Microsoft-IIS/6.0
X-Powered-By: ASP.NET
Connection: close
For there are zero day exploits against Microsoft's wonderful web server software. They've been out there for years now. Everyone knows those servers are being hacked. And yet no one has yet figured out how - AND NO: NOT EVEN MICROSOFT.
And these zero days are customised to attack PCs running Microsoft Windows. Of course they are.
See Also
The Technological: Wsnpoem
Security Fix: Fun with Spam Subject Lines
|