Home » Industry Watch » Coldspots
Security Update 2006-007Getting root without authorisation on OS X? It's not new.
[Note: See the articles AdminAuthorization and runner first if you haven't already.]
From the end of the 'Installer priviliges' [sic] discussion at Apple forums 30 November 2005.
kullerhamPster:
According to this description of the latest security update, the Installer issue got patched:
http://docs.info.apple.com/article.html?artnum=304829
Matt Broughton:
It has indeed been fixed. You will now be prompted for admin user name and password to elevate privileges if the package is incorrectly set for Admin Authorization when it actually requires Root Authorization.
So then everything's fixed, right? Wrong.
A user land process was indirectly generating a root process which could have taken over the entire machine. This is a design flaw - a dangerous one.
The root process incorrectly handled install configuration settings and gave away the computer - this was an implementation flaw. A programming error. That's all that's been fixed.
The underlying hack - for it is a hack - that makes this possible still remains. It's extant on Tiger 10.4, Leopard 10.5, and Snow Leopard 10.6. The strings/grep dump makes this apparent. The module 'runner' is part of Install.framework on all three platforms and makes it patently clear it expects to run as root.
0000000000097380 Install's runner tool is not properly configured as a setuid tool.
0000000000005fc0 Fatal error: unable to execute runner tool as root-user.
0000000000006000 Fatal error: unable to execute runner tool in group 0.
But the running of this 'runner tool' root process comes from a user land process.
runner is configured on all three platforms to be owned by root:wheel with permissions 6755 - both the SUID and SGID bits set. It's found here on all three platforms.
/System/Library/PrivateFrameworks/Install.framework/Versions/A/Resources/runner
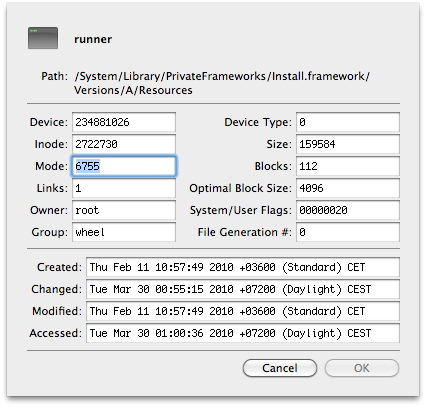
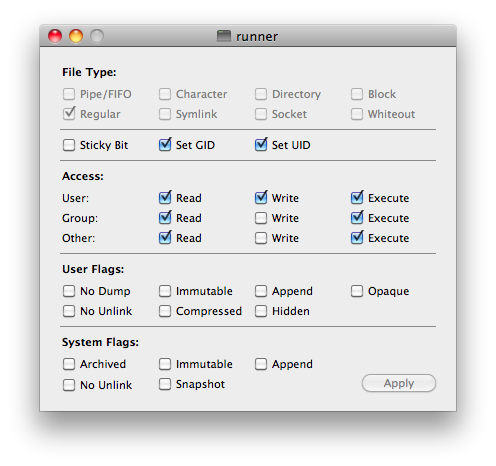
For those having difficulty interpreting the permissions bits:
There's no real difference between what Apple did back then, what they did with the Opener hole and the system login items hole, and what they're doing now with the Safari 4.0.5 and OS X 10.6.3 updates. They're getting root on your computer without your explicit authorisation.
'From the owner-user perspective this is horribly irrevocably bad. Anything that moves away from the enshrined concepts of user privileges is the thin end of the wedge and I'll have no truck with it. Ask me for my admin password goddamnit!!!'
'From the sysadmin perspective you can see the logic, if not the quality of the implementation. This is where Windows Domains excel (in design at least) whereby 'Administrator' means 'of the domain' and trumps Local Administrator. In this way a domain admin can roll out updates to the machines in the domain without requiring user interaction.'
In this case it's almost as if all 'local admins' of all Apple computers everywhere are trumped by a silent heretofore unknown but all-powerful domain admin: 'APPLEINC'.
Today they can already download software to your computer without asking your approval every time. Today they promise to tell you each time there's new software ready to be installed. But that's only out of the goodness of their hearts.
Up until recently they made a point of asking for your password and permission before doing anything sensitive on your computer. Up until recently...
Tomorrow they might be implementing the same (as yet unused) facility they have on the iPhone - to modify your files without you being able to do a damn thing about it.
Special Links
Rixstep Coldspots: runner
Rixstep Coldspots: AdminAuthorization
Rixstep Coldspots: .SoftwareUpdateAtLogout
Digg: How a Malformed Installer Package Can Crack Mac OS X
Mac Geekery: How a Malformed Installer Package Can Crack Mac OS X
'I didn't have to enter my password to update. Is this typical for everyone?'
- 'zapblast' at the MacRumors forums
'The media buzz over Opener went on the better part of a month and was then forgotten, but the fact remains that it is the single biggest security hole ever in the history of modern operating systems. No other operating system has ever offered such effortless escalation to superuser.'
- Rixstep Industry Watch on Opener 3.9
|