Home » Industry Watch
Tracker 2.0: Origins
Rixstep are releasing 'version 2.0' of their unique Tracker. Here a bit of the background.
'Never run unknown and untrusted software', goes the Apple mantra and as defensible as it seems it's not particularly logical. Not superficially. Bad software can at any time wreak havoc on a computer; if you've never run a program before there's very little you can do to prevent mishaps and deliberate destruction.
The ideal ('idea') is for admins to have a dedicated test box for new software slated for distribution - a box they can trash and rebuild rather than have to fix an entire corporate landscape. But even there the admins still need a tool that can tell them exactly what the 'unknown and untrusted software' is up to.
It's possible to do most of this from the command line. And that's in fact what staff have been doing here for years. Variants on the find command will find what new software touches and changes. But with a lot of software being tested it becomes tedium; and there are situations the command line can't cope with.
Zapping the Zapper
The brilliance of applications like AppZapper is that they don't need to be on disk when you first run the software you now want to remove; the gaping hole in this idea is that they weren't on disk and have no idea what your software actually did. They can only guess.
They can guess by going in the application bundle, plucking out the bundle identifier, and looking around for preferences files with that name; by looking in recurring locations such as '~/Library/Application Support' for anything similar in name; and by possibly scouring your entire home area for other similarities. Naturally they don't delete or trash anything without asking you first: they're only guessing.
But the number of related locations programs are using is growing all the time. Relative newcomers include '~/Library/Caches' and '~/Library/Caches/Metadata' to name but two examples - and this of course is only if the software in question is benign and otherwise 'plays by the rules': there's no way the 'zappers' can get at other 'legitimate' matters such as externally installed frameworks and the like.
And all bets are off if the software tries anything else or if the software is malicious. The 'zappers' do only a quick heuristic search - something you could do on your own. But they can't get at everything and by definition won't.
Finally: the zappers only attempt to remove software - they have no clue what happens in your system. They're not trying to. And as a result they don't see what really happens.
Tracker works the same way as the command line methodology: it compares time stamps on files with a 'beginning' time stamp to see what's changed in the interim. And it can therefore see what really happens. Tracker sees everything.
Prior to Tiger
Apple's HFS file systems have historically allowed hackers to cut under the security and wipe their tracks on their way back out. Unix file system stamps for last access, last change, and last modification are not all programmable. The 'last change' field may only be set by the operating system itself. This affords the required level of security. But all bets were off with HFS before Tiger.
HFS has namely five time stamps to Unix' three: it has an 'access' stamp related directly to the Unix 'atime'; it has a 'contentMod' stamp directly related to the Unix 'mtime'; it has 'create' and 'backup' fields which Unix does not have; and finally it has an 'attributeMod' field directly related to the Unix 'ctime'.
Prior to Tiger all five HFS fields were accessible programmatically. And as three of these fields map directly into the Unix file system API hackers were effectively able to modify files and then reset time stamps to hide their presence and intrusions.
Starting with Tiger that's changed: the 'attributeMod' field can no longer be set programmatically. But what does 'attributeMod' record?
'attributeMod' records any attempts to change file system information about a file including its time stamps. 'attributeMod' maps directly into Unix' 'ctime' ('last changed').
At the end of the day there is only one foolproof way to detect intrusion in user land: check the time stamps. Starting with Tiger no one in user land can escape detection.
create contentMod attributeMod access backup | HFS
------ ---------- ------------ ------ ------ o ---
x mtime ctime atime x | Unix
Spotlight Doesn't Know How to Do It
Spotlight uses a daemon based technology known as fsevents to detect changes to a file system. But two things make it inapplicable for the task at hand: it's tailored for use by Spotlight only; and it can run amok.
fsevents sends back notifications of file system events to Spotlight. But Spotlight only wants to know about changes - it isn't interested in what files are merely accessed - whereas infosec people are.
And fsevents can run amok: the FIFO buffer fsevents uses can overflow. One of the most important event notifications fsevents can send back to Spotlight is 'we're toast dude'. This happens when events come in at too fast a rate and Spotlight can't pick them up in time. When the buffer is full fsevents pushes out the oldest events not yet picked up, puts in the new ones, and sends its special message.
Whereupon the Spotlight client is again forced to crunch all connected file systems on its own to catch up. And that's obviously no good for infosec people or a program like Tracker.
Tracker doesn't need to use a daemon; it doesn't need to fetch event records at a bewildering pace or even at its own leisurely pace. It just sits and waits until everything's over and then checks what's happened.
Greeting You
Tracker's first of many windows is discrete: it has an empty table view and a bunch of toolbar buttons. The buttons say 'Go', 'Track', 'Stop', 'Info', 'Delete', 'Open', 'Paths', and 'Stamps'. The File menu reveals a number of additional commands such as 'Target', 'List Accessed', 'Track Info', 'Export', and 'Terminal'. The Edit menu has the commands 'Next Bold' and 'Previous Bold'.
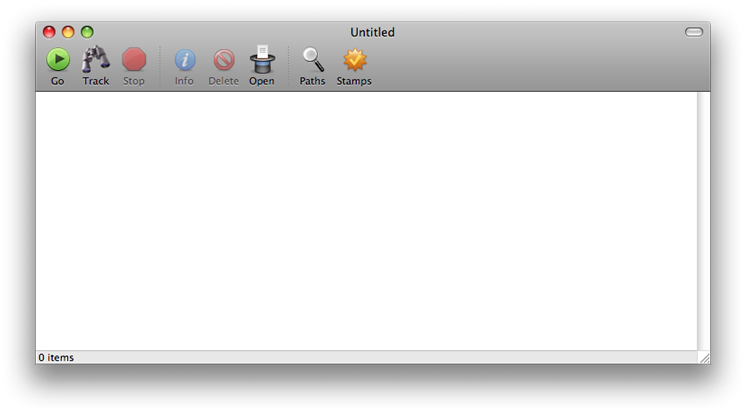
Quite a lot packed in there; where to start? As always: 'at the beginning'. Let's assume for now you have a recently downloaded piece of 'unknown and untrusted software' and you want to monitor carefully what happens when it runs.
- You can drop the software's application bundle directly on Tracker's dock icon.
- You can launch Tracker and drop the software's application bundle directly on Tracker itself.
- You can launch Tracker and use the 'Target' command on the File menu to navigate to your software's application bundle and 'load' it.
At this point the title of your Tracker window will have changed to reflect the target you've chosen. You're now ready to go.
Go
All you need to do at this point is click the 'Go' button on the toolbar. Relax - nothing happens at this point. For before anything happens you'll have to first declare you're 'really really sure' of what you're doing.
Which coincidentally gives Tracker an opportunity to analyse the contents of the application bundle you've chosen to target. Even if an application looks straightforward it might not be so. Pranks aren't widespread on this platform but they do happen. There have been trojans disguised as MS Office test drives on Limewire that actually hosed hard drives; malware such as Oompa Loompa; and the innumerable tricks used to get Opener on unsuspecting systems.
If a file looks like an image file but is not and actually runs an embedded Unix command to destroy your computer - Tracker will tell you about it beforehand. Tracker always shows you exactly what will happen if you choose to proceed.
And it's at this point you can sit back and play with the new software until you're satisfied and you've tried everything at least once. You exit the application and return to Tracker.
Track
The second button on Tracker's toolbar is 'Track'. Once you exit your target application you click this button. Tracker now scans your file system for things that have happened since you launched your 'unknown and untrusted software'.
Tracker will see both files that have been modified, files that have been added, and files that have merely been read. Most importantly it will see attempts to obfuscate any time stamps on your files or directories.
It's now that Tracker's table view begins to fill up - at times rapidly. Files that have been merely read appear in an ordinary font; files that have been modified or had their system info (including time stamps) programmatically changed will come up in a bold font.
[You can at any time stop Tracker by clicking the 'Stop' button but it's not advised. Yet if you do you can always start again by clicking the 'Track' button again.]
Once Tracker has completed its run you can go about inspecting what's happened with your new software - whatever's happened it's recorded here. And you can export the complete findings in a well organised easy to read text format for future reference.
[A good idea with even the most benign software is to keep this exported report inside the target application's bundle so you can refer back to it the day you want to uninstall.]
File Manager
Tracker also functions as a mini file manager. You can drag listed items to dock icons, to other applications, to the trash, and so forth. You can even drag an item from one Tracker window to another Tracker window to use it as a new target. You can 'recycle' and 'destroy' any item or selection of items by clicking the 'Delete' button.
Paths
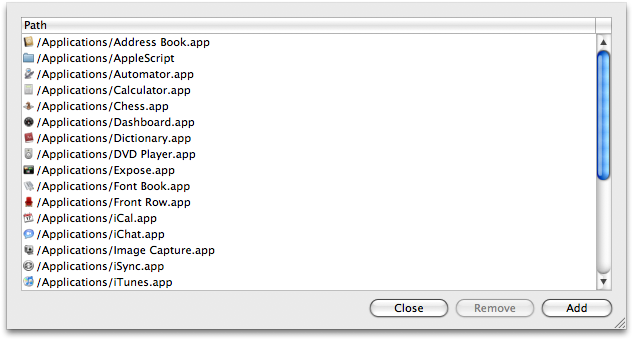
Most important for use of Tracker is setting the paths it will track. Tracking an entire system is time consuming (although 100% effective). If you don't give away an administrator passphrase to the new software there are only so many places where it can go and muck things up.
[Even without a passphrase software can read files that are otherwise 'off limits' but the basic rule is these files are identical on all systems, remain untouched by you, and so are of no interest to the hacker.]
If you don't give away your passphrase there are still two places software can both read and write: your home area ('~') and '/Library'. And for this reason both paths are default in Tracker. But you can change this if you need to.
Clicking the 'Paths' button opens the Paths sheet. Here you'll see listed the paths you've chosen to have Tracker inspect. You can remove as you want and add as you want - the latter by clicking the 'Add' button and using the standard file navigation dialog.
Redundancy is completely circumvented: if you already have '/Applications' then adding '/Applications/Utilities' yields nothing as it's already included. Likewise if you have only '/Applications/Utilities' and then add '/Applications' to your paths '/Applications/Utilities' will automatically disappear from your listing.
Each set of paths is unique to each Tracker window in case you have several Tracker sessions open simultaneously.
And if you do decide to give away your passphrase to the 'guest' software then set your root directory in this Paths sheet. This will of course automatically remove all other paths when it's added.
What happens if you forget to change the paths before you launch your untrusted software? Nothing - you just change your paths after the fact. In fact you can even exit Tracker and come back to the matter later.
Rude Software
Some programs do nasty things. Some software products are obnoxious and rude. Some of them will only ask you to close all other programs first (and refuse to run until you've done so) and some of them will actually go and kill off all your other programs with or without prior approval. Some programs are so poorly written (or maliciously written) they'll set about doing not only the above but also wreaking destruction around them.
None of the above really matters to Tracker. In fact keeping Tracker open as you run your untrusted software remains as a convenience only: Tracker can at any time return and resume things where last you left them.
Stamps
'It's a LOT of fun to play with. Open a gazillion windows all at once. Hit Go in rapid succession on one. Keep answering 'really sure' to the dialogs. When you've got a few hundred stamps you open all the stamps sheets on all windows at once and then start playing around with them. Perfect synchronisation. Also try opening a new window and clicking 'Go' in that and watch all the other listings jump. This beats the card game Solitaire any day. ;)'
Tracker namely keeps a 'pool' of previously used tracking stamps in its repository. Click the 'Stamps' button to see it. This is a list of all tracking stamps you've used sorted with the most recent first and displaying the targets (if any) of these tracking sessions. [It's of course possible to run Tracker without an explicit target: you can for example start Tracker when you log in and wait until your next login to see the changes.]
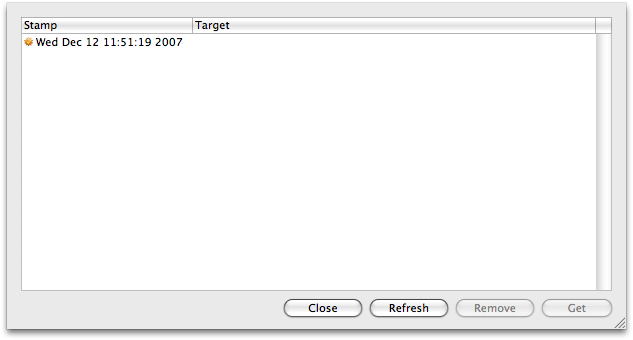
You can of course edit this list and remove any stamps you no longer want (but you'll be warned when you do as this is an irreversible action). And you can 'get' any stamp in this list to use to begin tracking again.
Tracker saves your tracking stamp anytime you click that 'Go' button on its toolbar. There's no way malicious or stupid software can trip you up. If your system is rebooted - fine: just go back and get the stamp that started it all off and track again. No worries.
The stamps listings are a common repository: all stamps generated by all Tracker sessions are here. The stamps listings are also perfectly synchronised: any changes to any one window's listing is automagically reflected in the listings of all other windows. Try opening a number of Tracker windows and see.
Stamps currently in use by an open Tracker session will of course not be removed: if you choose to remove all stamps and see one or two remain afterwards this will be why.
Further Commands
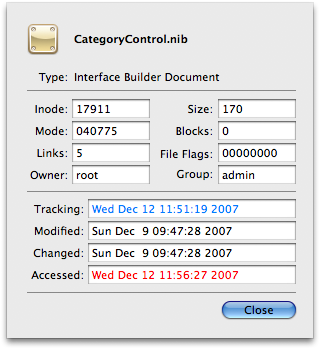
To give you a better look at what's happened Tracker has a special Tracker Info sheet. Select any one item and choose 'Tracker Info' from the File menu. The name and icon of the item will be displayed along with its shell defined type, its inode, mode, number of links, owner and group, file flags, size - and then its three Unix time stamps with the tracking stamp at the top listed in aqua. At least one of the time stamps will be displayed in red: these are the stamps which are later than your tracking stamp.
You can also access the standard ACP file info sheet by clicking the 'Info' button on the toolbar. Here you'll find a lot more - everything not listed in the first sheet. You get the full path to the item, its device and file generation numbers, device type, and the three Unix time stamps.
 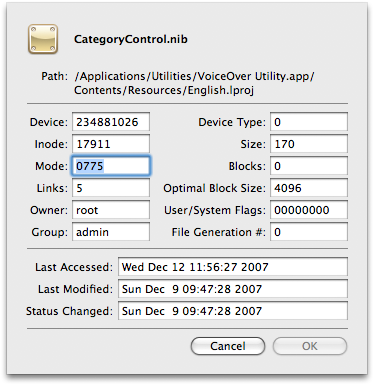
You can also click the 'Open' hat to better get at mysterious items in your listing. You get a discrete sheet to either open a selection in Tracker but with another editor, run any program (without having to know the complete path or appending '.app') or opening any document at all with or without its default editor or default viewer.
If you're not interested in seeing all the files that have been only read and only want to see the files that have been tampered with - just toggle 'List Accessed' on the file menu. And if you're listing all files and want to fast forward to the modified items - hit 'Next Bold' on the Edit menu. Go back through the list using 'Previous Bold'.
If you need to drop to a command line at any time in relation to something you're looking at in Tracker - then select it and then choose 'Terminal' on the File menu. Tracker will drop you into the nearest possible directory in relation to the item you selected.
There are also a number of search functions on the Edit menu. Finally you can (and should if it's important software) export your tracking session - 'Export' on the File menu. The default extension is 'track' and the ACP system text editor Rixedit will automatically pick it up.
All data relating to your session are recorded here: your starting time, stopping time, target, and all paths searched. Files accessed, changed, and modified are listed under separate headers.
Review
So let's see if we can review what we've learned - and add to the mix.
- Tracker is unique: there's no program like it on OS X, probably not on other platforms either.
- Nothing escapes Tracker - not even malicious software as long as you haven't been 'rooted' - because nothing can escape your file system. As long as you're running Tiger or better.
- Tracker works by comparing time stamps: it compares the three Unix time stamps on files with the tracking stamp for your session start. Anything listed at that exact second or later is included in Tracker's cull.
- When listing accessed files you'll see a lot of things you didn't know were being affected. Applications use external frameworks and consequently you'll see elements of these frameworks listed. And so on. When looking for evidence of stealth activities such as 'data mining' you'll naturally have to disregard 'legitimate' accesses such as these.
- If you give away your admin passphrase to an installer or other program you must of course track from the root of your file system - and in particular check your '/private' and '/System' hives afterwards. This takes a bit more work but after all you did ask for it - you gave an unknown guest full access to your machine. Possibilities for lurking/corrupting '/System' are myriad; use 'Next Bold' and 'Previous Bold' to see what's actually been modified to start with. Do the same for '/private' which holds a lot of system configuration data that could be corrupted against your best interests.
- In particular look for things happening in '/System/Library/StartupItems', '/Library/StartupItems', and '/Library/InputManagers'. Something planted in one of these directories - locations programs like the 'zappers' won't get within a mile of - can be an indication of foul play.
- If your software comes bundled with an installer then look inside the installer if you can before you run it. Some types will include property list files that fairly explicitly outline what will happen in realtime. And be sure to track the installer and actual application separately - you need to know what both programs do but you want to keep tracking of the installer client separate for future reference.
- Just because your friends say an app is OK is no reason to trust it: find out for yourself what it does and where it does what it does and then you might trust it too.
- Remember the old adage: 'never attribute to malice that which can be explained by pure outright stupidity'. There are enough idiots passing off 'software' on this platform; don't trust them. The best way to build up trust is by giving away none and always tasking responsibility where it belongs.
 At least today you have a tool to make that task possible. At least today you have a tool to make that task possible.
Availability
Tracker 2.0 will be available on 2 December 2007 with the following software packages: ACP, ACP Academic, Xfile, Xfile Academic. It will also be available for testing as part of the 'Xfile Test Drive' starting in January 2008. See below for further details. Current subscribers receive Tracker 2.0 as part of their normal subscription.
Further Information
Tracker: No Escape
Rixstep: Xfile Test Drive
Rixstep: Buy the Software
|