Home » Learning Curve
EasyDoc QuestionsThe journos don't ask the questions, only the users do.
MACUNIVERSE (Rixstep) — The 'Mac community' got hit by another virus. Except it's not a virus. It's a trojan.
For those unfamiliar with the terminology, a trojan, which takes its name from a famous Homeric horse, is bad software disguised as good. A virus, on the other hand, is a contagious 'POS' which comes attached to binary executable code, goes 'resident', and then tries to infect other executable files (or boot sectors).
EasyDoc Converter has been available at MacUpdate. This has been possible because the MacUpdate proprietors, in an effort to push out competition, have used the practice of publishing software first and only checking for malware afterwards.
[MacUpdate also had a bad habit of disallowing software titles that inadvertently implied there's something wrong with the US invasion of Iraq. Ed.]
Although the download's finally gone, the listing's not.
EasyDoc Converter seems to have spread enough to cause consternation, alarm, and a good deal of reporting opportunities for the tech media, as well as providing attractive selling points for the AV industry.
EasyDoc was supposed to be able to convert FreeOffice and SimpleStats files to Microsoft's DOCX through a (to say the very least) simplistic graphic drag-drop interface. To wit:
But of course it did nothing of the kind.
The best run-through of EDC was compiled by Bitdefender, where in typical fashion EDC was given a classy name: Backdoor.MAC.Eleanor. (Apologies to Eleanor.) The front end is simplistic, created with Sveinbjörn Þórðarson's Platypus. Once you accede, the stuff gets nasty.
But how nasty? Although the trojan has received wide media coverage, no one's seen asking the all-important question until one gets over to MacRumors.
A selection of choice links.
http://www.cultofmac.com/436670/dangerous-new-mac-malware-fully-compromises-os-x/
http://www.tomsguide.com/us/mac-malware-easydoc-backdoor,news-22936.html
http://www.theregister.co.uk/2016/07/05/easydoc_malware_adds_tor_backdoor_to_mac_systems_for_botnet_control/
http://arstechnica.com/security/2016/07/after-hiatus-in-the-wild-mac-backdoors-are-suddenly-back/
http://www.cnet.com/news/new-mac-malware-discovered-in-the-wild-installing-backdoors/
http://www.idigitaltimes.com/new-mac-malware-eleanor-hijacks-facetime-emails-and-more-543957
http://www.digitaltrends.com/computing/apple-mac-backdoor-phony-file-converter-app/
The Big Question
But what can be seen, the 'Big Question' is asked nowhere in the tech media. TidBITS passes the buck to more knowledgeable sites after a brief intro with truisms such as 'be extra careful' and 'stick to software from reputable developers', a reminder how Microsoft responded to the Love Bug ('don't click on email attachments'). And the site of Graham Cluley (what a name) fans the flames even higher by repeating 'Dark Avenger' claims made by Bitdefender such as 'the possibilities are endless'.
'Someone can lock you out of your laptop, threaten to blackmail you to restore your private files, or transform your laptop into a botnet to attack other devices. The possibilities are endless.'
Of course they can, but once again, no one's asking the Big Question, much less giving readers an answer. For that, one has to go over to the MacRumors forums.
forums.macrumors.com/threads/what-you-need-to-know-about-mac-malware-backdoor-mac-eleanor.1981326/
When you open the app, does it ask for administrator password? Seems like a well designed malware.
- miknos
Because after all is said and done, after all the journos file their pieces and go home, it's about the password.
- If no password is required, that means one of two things.
- Either the damage is minimal (but still significant); or
- Someone finally found a way to hack Apple's Software Update helper.
- If a password is required, then, given intelligent users out there, EDC can't present a significant turbulence, for people in general won't be so stupid as to grant virtually unlimited access to their machines (where they themselves will most likely not be able to go) without proper vendor vetting.
Any app/process running on an admin password (from an admin account, the default account) can do virtually anything, save a few things reserved for single user mode (SUM). It can go anywhere, do anything, and you'll have to find out where it's gone and what it's done. Searching tens of thousands of directories. In short: you don't give out the keys to your computer to just anyone. Full stop. Good luck, sucka.
Hyping the Undesired
Macs don't need antivirus. EasyDoc Converter isn't a virus anyway. Mac users need intelligence. Anyone can fool anyone, so don't be fooled. Tom's Guide makes the following claim:
You need an antivirus program on your Mac. That statement may cause some Apple users to shake their heads in disbelief, but with the amount of Mac malware on the Internet today, this fact is no longer up for debate.
That statement is patently false.
Trusting Unknown Software
No, you can never trust unknown software. You can't even trust Apple's App Store (MAS). MAS gets a good going-over in the MR forums. More and more users find the App Store unsatisfactory, as they do Apple's dubious Gatekeeper.
Developers are wary of MAS because:
- They can't be guaranteed they can get out bug fixes;
- Apple take three times the commission of ordinary payment processors; and
- Their code is no longer their own.
That last point bears explaining. No software vendor can be held to account if middlemen - even Apple - get their hands on their products. Yes, even the binaries. No respectable software vendor would ever let others get access to it.
Apple may have a nearly impeccable reputation, but does that hold for each and every employee? Are Apple employees 'bonded'?
Some software sites offer click-throughs to vendor sites where software can be downloaded; any software site requesting a copy of a product is immediately and categorically suspect. Full stop.
The Need for Rollback
Shit happens. Mistakes will occur. Users need to know how to recover if and when disaster comes their way. Your first most trustworthy friend is your command line.
-newer file
True if the current file has a more recent last modification time than file.
Do like this. Download your new app and close all apps you can. Run your suspect app, go through its options and settings, exit. Now run the find command from your user root with the flag -newer with its parameter being the file you just downloaded.
find will tell you what's happened to your file system since you completed that download - tell you everything, no exception.
Redirect find's output to a file you can study later.
find ~ -newer ~/Downloads/<YOUR DOWNLOADED FILE> >~/Downloads/find.out
You can make sure find doesn't bail out on an 'access denied':
sudo find ~ -newer ~/Downloads/<YOUR DOWNLOADED FILE> >~/Downloads/find.out
Then you can study find.out to see what's happened. It might be tedious, but it's total.
A Plug
This is a plug, but it does have a point. And above all it holds a second vital question: why has no one else done this? Surely people aren't relying on 'app uninstallers' to do their dirty work? For there's a correlate to find, here, and there's a version that's free too. There should be a lot of competition out there, but there is none. Users have no tools with which to repair their systems.

find has come a long way, but it's still command line. And that means not only that it's not GUI, but that it's only one thing at a time, and most of the work has to be performed manually (by you).
Testing unknown software: start by finding out how it'll launch before you launch it. This is possible through the Cocoa (NeXTSTEP) APIs. One of the more recent 'attacks' on Macs uses the ruse of a misleading filename.
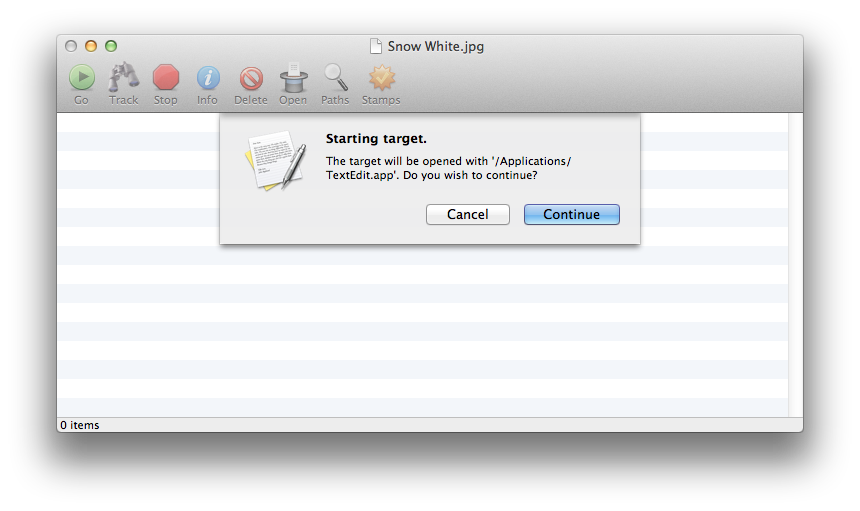
Tracking unknown software: Tracker does what find does, but it also sets an upper limit. So you're looking for file system changes within a given interval. The start of the interval is when you start running the suspect app; the end is when you use Tracker to track the changes.
With find, you have to manually go through the output file to see what's happened; Tracker gives you an interactive interface so you can inspect files and metadata, and remove (or move) the stuff you don't like.
Tracker will also show you what's happened to the file time stamps, so you know what's going on.
Try it.
Memorable Quotes (from MR)
When you open the app, does it ask for administrator password? Seems like a well designed malware.
- miknos
Sooooo... don't download Firefox, LibreOffice, or any other open-source applications that aren't allowed on the MAS for licensing reasons?
- FoxBJK
Another benefit is that the dev gets all the revenue versus Apple getting a cut.
- steiney
Sadly I had to disable GateKeeper too as it was blocking too many legitimate apps. I never use it now.
- AtheistP3ace
How can one be 100% sure about what exactly the software will do, before even having used it?
- baryon
The fact that MacUpdate send you their updater App NOT the file you asked for killed MacUpdate for me. ANY system that does this is a malware site and can no longer be trusted.
- ulyssesric
Should I have some other apps to secure my Mac? Any recommendations?
- Oblivious.Robot
Bless those who are able to survive by using only app store programs on their MacBooks and iMacs. But some of us have to use 3rd party programs because the app store is lacking of a lot of programs.
- nia820
It's impossible no matter what... I mean VLC, Handbrake, any pro app that is non-Apple, any browser that is non-Apple... even Office... is outside the store.
- ppcebay

|