Home » Industry Watch » Coldspots
What's Wrong with This Picture?Getting root without authorisation on OS X? It's not new.
28 November 2006: Apple finally recognised a 'transgression' against Mac users in their Security Update 2006-007. The 'transgression' was reported in the Apple discussion forums and deconstructed by Adam Knight of Mac Geekery.
Apple's Installer.app was letting unauthorised install scripts reach and subvert system-protected areas.
The advisory makes it clear the 'flaw' went back to at least 10.3 Panther.
Installer.app's Install.framework contains a curious critter known as 'runner' that won't run unless it's as root - this despite Mac users perhaps never being asked explicitly for authorisation.
0000000000097380 Install's runner tool is not properly configured as a setuid tool.
0000000000005fc0 Fatal error: unable to execute runner tool as root-user.
0000000000006000 Fatal error: unable to execute runner tool in group 0.
To recap: double-clicking a 'mpkg' or 'pkg' file will automatically launch a root process without explicit authorization.
But Apple told everyone they 'fixed' this on 28 November 2006.
Following are two screen caps. Both of Activity Monitor. The clues are in the selected rows. The caps are taken before and after 'Software Update...' is selected from the (apple) menu. What's wrong with the second picture?
Clue: the answer's in one of the selected rows.
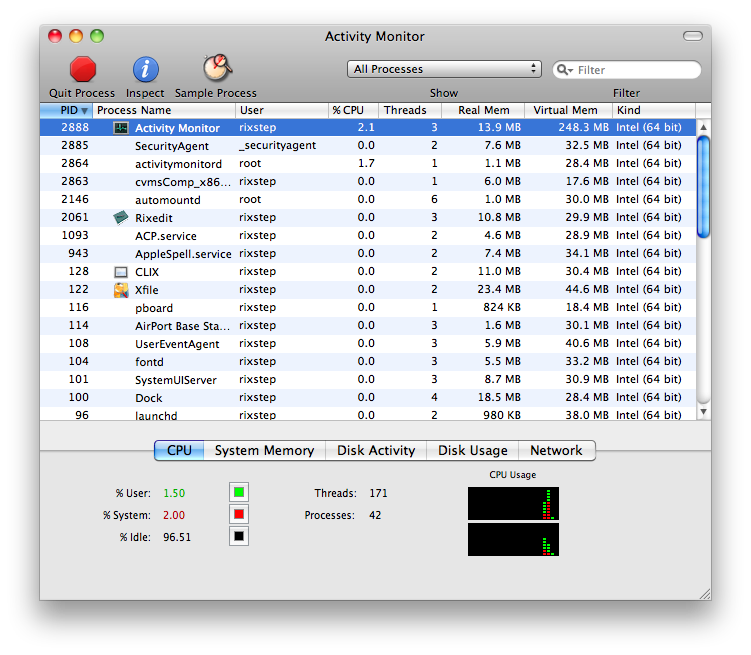
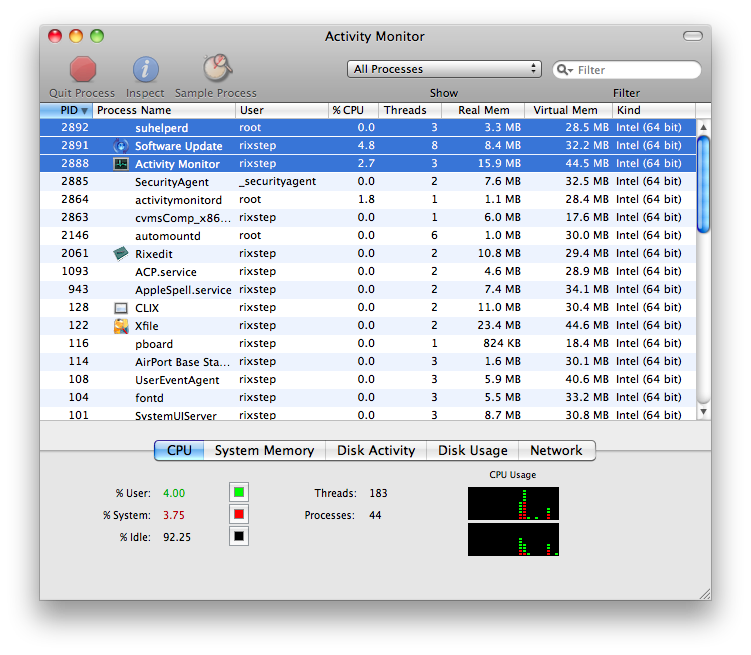
Special Links
Rixstep Coldspots: runner
Rixstep Coldspots: AdminAuthorization
Rixstep Coldspots: .SoftwareUpdateAtLogout
Digg: How a Malformed Installer Package Can Crack Mac OS X
Mac Geekery: How a Malformed Installer Package Can Crack Mac OS X
'I didn't have to enter my password to update. Is this typical for everyone?'
- 'zapblast' at the MacRumors forums
'The media buzz over Opener went on the better part of a month and was then forgotten, but the fact remains that it is the single biggest security hole ever in the history of modern operating systems. No other operating system has ever offered such effortless escalation to superuser.'
- Rixstep Industry Watch on Opener 3.9
|