Home » Industry Watch
2010-003Small but fully packed.
There's a new security update, says the one. O RLY? says the other. Best to check.
It's only 6.5 MB so it downloads in seconds. This must be really important, says the one.
Tracker's run on it. And things are stopped halfway just to pick up the odd file name or two.
 No password required. Again. No password required. Again.
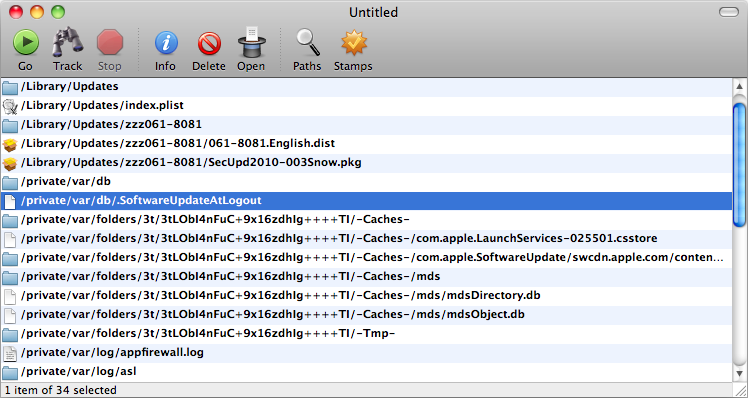
After that it's to check what's been changed. Which mostly comes down to 14 files - the ATS framework.
'14 items, 17923511 bytes, 12464 blocks, 0 bytes in extended attributes', says the drop.
The name of the install package is 'zzz061-8081'. 'SecUpd2010-003Snow.pkg' is placed in /Library/Updates.
'Security Update 2010-003 is recommended for all users and improves the security of Mac OS X', says 061-8081.English.dist.
The file also lists target architectures as 'ppc,i386' despite the machine being 64-bit.
Authorisation is specified as 'Root'. Restart on conclusion is required.
One of the SU components looks in the system keychain. /etc/authorization reveals nothing.
34 files have been changed before logout.
Tracker runs a second time when the system comes back up again. This update's been all about the ATS framework. Apple Type Services take care of fonts.
14 items, 17923511 bytes, 12464 blocks, 0 bytes in extended attributes.
ATS.framework/Versions/A
ATS.framework/Versions/A/_CodeSignature
ATS.framework/Versions/A/_CodeSignature/CodeResources
ATS.framework/Versions/A/ATS
ATS.framework/Versions/A/Resources
ATS.framework/Versions/A/Resources/Info.plist
ATS.framework/Versions/A/Resources/libATSServer.dylib
ATS.framework/Versions/A/Resources/libFontParser.dylib
ATS.framework/Versions/A/Resources/libTrueTypeScaler.dylib
ATS.framework/Versions/A/Resources/libType1Scaler.dylib
ATS.framework/Versions/A/Resources/version.plist
ATS.framework/Versions/A/Support
ATS.framework/Versions/A/Support/fontd
ATS.framework/Versions/A/Support/genatsdb
No lproj files to clean out, no nothing. The update's finished almost before it began. So what was it about? Try Google.
Any more?

'Unspecified vulnerability in Safari 4 on Apple Mac OS X 10.6 allows remote attackers to execute arbitrary code via unknown vectors as demonstrated by Charlie Miller during a Pwn2Own competition at CanSecWest 2010', says the US NVD.
Oops. So Charlie got a third MacBook and some cash from Tipping Point, Tipping Point got an exploit, Tipping Point sold an exploit to Apple, and three weeks to the day Apple pushed out a patch for it. Not totally good but not totally bad either. IE8 users (are there any?) are still waiting for their patch...
Forbes went on the attack against Apple already on the day after the contest, writing 'Miller applied NSA skills to exposing Apple's Swiss-cheese security'. (No one from ZD was involved in the article.) But author Andy Greenburg does point out that Apple is Charlie's platform of choice.
 Comments at the Forbes article get rowdy. Comments at the Forbes article get rowdy.
'Articles like this pop up every few years', reasons 'MajorWebUser' the following day.
'The purpose is primarily sensationalised self-promotion.'
'Applying the same fears and concern for cyber security to our homes, the authors would have us armed with an array of motion sensors, heat sensors, microphones, pressure plates, laser triggers, guard dogs, and a private security team on call 24/7.'
'Talk to any cop and they'll tell you that a set of solid deadbolt locks and common sense will do the job.'
Well actually all they said (with a bit of hyperbole) was that Charlie Miller found a bug again and Apple fixed it.
'I've never seen such a breach on a Mac system', adds 'MajorWebUser'.
Well actually you did. Right here. Or in Vancouver. That's why Apple fixed it.
'The Windows Fanbois get all aflutter about this stuff, it must really hurt watching these last 9 years OS X continue without even ONE virus', posts the mysterious 'NotTellinYou' who evidently isn't planning on revealing his real identity. 'To me if a guy that knows more about security than I ever will uses a mac, I feel pretty good using one too!'
Well yeah sure - but take the update anyway, OK?
'I've watched a Fortune 500 security expert in Detroit try to execute code on an Xserve without proper credentials', posts 'uruzone'. 'He couldn't do it.'
What was the name of the company?
'In fact, in all the years (25) that I personally have been using, installing and supporting Macs [...] I've not seen a SINGLE instance of a Mac being infected by spyware or malware.'
Somebody with pants on fire has a nose growing longer than a telephone wire.
'To the person who thinks Charlie Miller is being deceptive I can tell you he is not', jumps in 'joe6620'. So now 'uruzone' is back.
'This guy's accomplishments have been falsely reported over and over by leaving out the one CRUCIAL bit of information that this article does its level best to gloss over: THE EXPLOITS REQUIRE USER INTERACTION. Just navigating to a website can NOT infect your Mac and install spyware through Safari. ANY process that happens at the system level REQUIRES an administrator's name and password.'
Such a shame 'uruzone' isn't planning on revealing his real identity.
Bob McMillan finds an article by Gregg Keizer at Computerworld that's interesting.
'Miller exploited ATS through Apple's Safari browser, which accesses ATS code libraries to draw text. Last year Miller also exploited ATS at Pwn2Own.'
Moz won the race, patching their Vancouver hack in 8 days. Apple follow at 21 days. Microsoft still haven't passed the finish line.
See Also
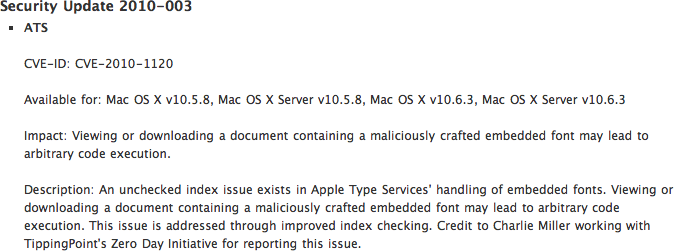
About the content of Security Update 2010-003
APPLE-SA-2010-04-14-1 Security Update 2010-003
National Cyber Alert System: Summary for CVE-2010-1120
Forbes/Greenberg/Trend Micro: The Mac Hacker Strikes Again
|