Home » Industry Watch
More on Mac Defender/MacGuardDetails are too scarce.
Word has it as many as 150,000 Mac users have been hit by the Mac Defender/MacGuard. Yet details about how it works are scarce and Apple aren't telling. And neither are antivirus companies. Here's a rundown of what Apple and news sites have to say.
Daring Fireball/John Gruber
Daring Fireball's John Gruber has studiously avoided the topic, linking only to a type of Jim Jones 'soul massage' with no technical information or advice whatsoever. This is probably best: HD Moore long ago exposed Gruber as knowing nothing substantial about computer security.
Huffpost Tech
Huffpost Tech: Makers Of Mac Defender Release New Malware
After a user visits an infected webpage, the computer automatically downloads a file that runs an installer for a program called MacGuard. The install does not require a username and password. Apple's instructions to prevent the Mac Defender attack asks users not to enter administrative passwords - but they are no longer necessary.
Apple say they'll have a fix for the previous version in their own next release but that's only going to be patchwork and not a real solution. As for what Mac Defender does now, Apple won't have a solution until they roll back the feature requests of their 'user experience engineers' and start acting like grownups.
Huffpost Tech: Apple Acknowledge Mac Defender Malware, Promise Mac OS X Update
Apple acknowledged in a statement that Mac Defender malware, a phishing scam that tries to trick users into giving their credit card information, could have affected between 60,000 and 125,000 users.
Apple's release comes shortly after the Mac Defender malware issue first started to spike. At the time, the company told support staff not to help customers who came to them with the malware or even to admit to the existence of such malware.
NewsFactor Network
NewsFactor Network: New Mac Malware Variant Doesn't Need an Admin's OK
We'll give it to you straight. Santa Claus is a myth, the moon is green cheese-less, and Macs are vulnerable to malicious software. More evidence for the latter legend-buster is a new malware program that doesn't require a user to enter an administrative password to install it.
That's part of the story. But the oft-repeated bit about this savvy hack trying to install in /System/Library doesn't make any sense. There has to be more to it.
CNET UK
CNET UK: Mac Defender malware mutates in response to Apple's warnings
The new iteration of the nasty bug is called MacGuard; it doesn't require an administrator password to install itself.
Again: something's up.
CNET UK: Apple tell support staff not to confirm Mac Defender infections
Apple's support service AppleCare has been instructed to take a hands-off approach to customers calling about the Mac Defender malware. Staff are under strict instructions not to confirm or deny any infection by the malicious software, which Apple is currently investigating.
Support staff have also been told they shouldn't attempt to remove the malware. They're not to refer you any further and shouldn't send you to an Apple Store, which wouldn't be able to help anyway. They've also been instructed to refer you to the Mac App Store but not make any suggestions about which antivirus software to download from there.
Great. Only Apple could think up a tactic like that. Did Steve Jobs give the order from his sick bed? Or does everyone else there think the same way today?
CNET UK: Mac Defender fake antivirus software is first major attack on Apple computers
The old saw that Macs don't get viruses is under fire as a piece of malware called Mac Defender is rampaging across the Web. Claiming to be antivirus software, Mac Defender and its variants pretend to clean up your computer - but all they're after is your cash.
Mac Defender looks like a well designed, real piece of software, fooling users into installing it. Once it's on your Mac it starts opening porn sites to make you think you have a virus, and informs you of nasty spyware where in fact there isn't any.
If you enter your credit card details and pay for a subscription, the software stops with the porn, making you think it's defeated the nonexistent virus. The cunning rascal! Basically it's like that bit in The Lion King 2 where Kovu's pride put Kiara in danger so Kovu can manufacture a brave rescue. Yes it's exactly like that.
Apple Support
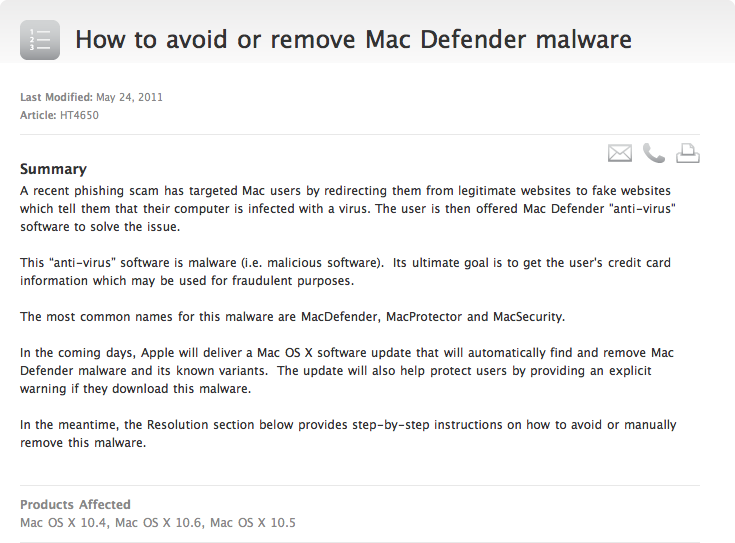
Apple Support: How to avoid or remove Mac Defender malware
In the coming days, Apple will deliver a Mac OS X software update that will automatically find and remove Mac Defender malware and its known variants. The update will also help protect users by providing an explicit warning if they download this malware.
Ho ho ho. That's fine with the earlier iteration but not with the new one. The new one installs straight away without prompting for password.
AOL News
[You need Flash here.]
TUAW
TUAW: MacDefender malware protection and removal guide
The MacDefender malware has been causing trouble for Mac users all over the world; people are calling Apple Support in a panic, spending time visiting their local Apple Store Genius, and getting all stressed out about it. What's worse: the malware is mostly harmless to your computer. It's a scam trying to rip off your credit card number, not hurt your Mac (not that the theft of your credit info is a good thing).
This willy-nilly approach might appeal to babes in the wood, but check the date: 19 May. This is before Mac Defender Gen 2 aka MacGuard hit. So all the information with all the pretty screen dumps is out of date and pretty worthless.
And ignorance never helps. There's a reason this happens on Mac OS X but not on Unix. Tricking a user's one thing. Anyone can be tricked, even on the most secure system. [See what Mendax did on the telephone.] But deliberately bypassing the user requirement to submit a password so criminal gangs can utilise the same method is not something that happens to Unix. Only to Apple.
Techblog
Techblog: More Mac malware madness: No password required
When Mac Defender first reared its ugly head, the malware program aimed at Mac OS X required a victim to enter the computer's administrative password to install it. That meant a user had to give explicit permission to put the program on a system.
No longer. A new variant of Mac Defender - this one known as MacGuard - doesn't require an administrative password to install. It is placed in the user's Applications folder rather than the systems level Applications folder, which does not require administrative permissions.
Somebody is smoking his beard here. There is no 'systems level Applications folder'.
Washington Post
Washington Post: Apple malware program evolves
MacDefender, the malware program that's tricking some Mac owners into giving up their personal information, has evolved.
The original program asked for a user's administrative password before it downloaded. Now a new program variant called MacGuard bypasses that step and puts itself onto your computer before deleting the original installer.
Asked for your password before downloading? It's a wonder anything gets fixed with the confused information being spread around by 'technical journalists'.
PCWorld
PCWorld: Mac Malware is Back. Your Move, Apple
Apple may have conquered the Mac Defender malware with an official support page and a promise to wipe out the problem through a software update, but that's not stopping malware authors from fighting back.
Don't bother reading this article. It's really dumb. As you can tell already from the headline.
What's Going On?
What's going on? That's the question. With Apple instructing support lines to pretend they don't even know what the thing is and with the greedy antivirus companies unwilling to share with each other and with the general hoopla and fanboy panic about the sky falling - who can know?
But a few things manifest themselves as self-evident.
- The various stories as told so far don't make any sense. There's no such thing as a 'systems level Applications folder'. Credit to whoever copied that from another site for being Eejit of the Week™.
- Where did the original variant install? And why? Does this pesky critter need root access for some reason? It makes no sense to ask for a password if root access isn't needed. Unless this was a configuration error with Install.app. But who knows and who's telling?
- Either this 'MacGuard' gets root access through a hole Apple introduced into their 'rock solid foundation' or there's basically nothing to worry about at all. If the exploit is simply about people being hoodwinked into installing bad software, then the system is not in jeopardy and everyone can go home. But if it exploits a security hole Apple either introduced or have been typically slow to patch, then Apple have some serious reckoning to do.
There should be no reason for Mac users to be careful what they click on. There is no way a Unix system can be exploited in that fashion. Unfortunately there have been several cases where Mac OS X systems have been vulnerable to exploit. Mac users need to make their voices heard so Apple in such case stop playing games with their touted 'rock solid foundation'. And get it back to 'rock solid' again.
See Also
Rixstep Coldspots: Statement on the MacGuard Exploit
|