Home » Learning Curve » Developers Workshop
Two IndispensablesOne is current, one is past, both are open source, both can still be indispensable.
Two Indispensables: Two apps no serious developer should be without. One is current, one is past. Both, given the right equipment, can still be indispensable. Both are open source. (See below.)
Taken in alphabetical order.
AppKiDo
This is the DIY course in Cocoa. No exaggeration that this app, together with Don Yacktman's book, are all a seasoned developer needs.
For Cocoa (NeXT's AppKit and Foundation) is eminently simple. It's that well designed. With many times the number of API calls of comparable platforms such as Windows. But you learn how one class group works and you've learned them all.
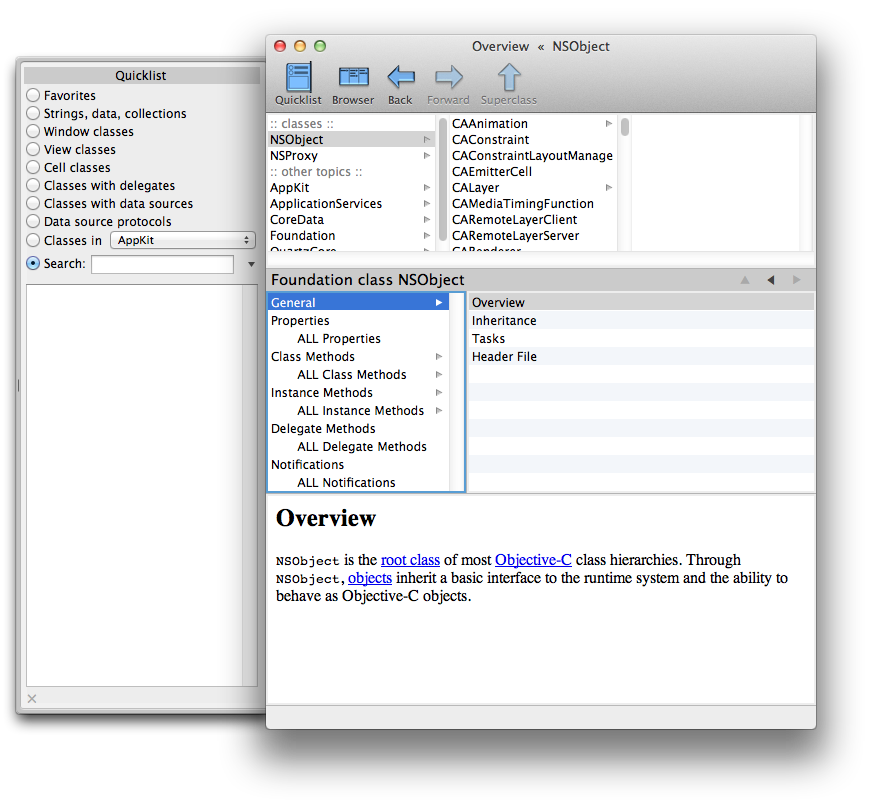
Apple's own documentation is not helpful. It's not written or organised in a way that makes it eminently searchable. Watching developers in a course struggling with the documentation, and seeing how much time is wasted just because explanations are foggy and pertinent info is hard to find...
Andy Lee did a fantastic thing here.
AppKiDo works with Apple's actual documentation, parsing it to smithereens, and reassembling it into something that can truly be used. AppKiDo's output includes the actual framework header files, and if you know anything about how those files are strewn about the filesystem, you'll begin to appreciate what Lee has done.
The app is no longer current, as Apple keep changing the structure of their documentation, just as they keep changing the location of their files, just as they keep changing just about everything. But if you have an older machine, it's worth using it to have the chance to meditate on Cocoa together with AppKiDo.
Everything is neatly sorted, unlike the confusion emanating from Cupertino, not only alphabetically, but by topic as well. Andy doesn't mix class and instance methods either - again, unlike that offered at iPhone HQ.
Cocoa was originally designed in Redwood City, by people that certain members of the 'community' don't like to hold in high esteem, yet it's of course precisely their efforts that led to NeXTSTEP (and OPENSTEP after it) being such a prize that Gil Amelio could pay $429 million for the rights, and no one's going to argue with the success of Apple today, running systems all based on Cocoa.
Learn how NSArray works. Wake up to the fact that it's static. Discover there's another class, NSMutableArray, that works with NSArray to give you - mutability. (And 'NS' is always there to remind you where it all came from.)
Then find out that NSString and NSMutableString work the same way. It's the same way to allocate automatics on the stack for all of them. The same way to set up globals. The same way to get rid of them when needed. And so forth.
And if you forget something, it's easy to find what you want with Andy's AppKiDo - unlike Apple's attempt.
This API is perhaps the best architectural achievement since Ken and Den fired up their console and terminal long ago. And AppKiDo is the best way to perceive it, to appreciate it, to grok what it really means. Effortlessly.
What a shame that Lee can't keep it up. The thing leaks like a sieve too, but it's far and away the best software tool out there for those keen on learning Cocoa.
Hex Fiend
A product of Ridiculous Fish. They win you over immediately with their great corporate name. Hex Fiend is a hex editor like you've never seen, and we can attest, having built several ourselves over the years, albeit for more primitive platforms.
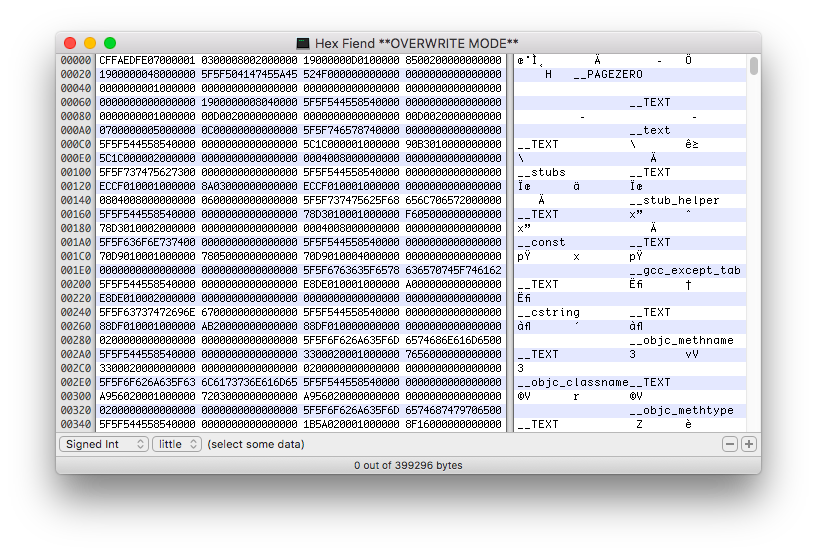
These are some of the things that will blow your mind. They're all taken from the product page. Yes, you have to see this app to believe it.
- Insert, delete, rearrange. Hex Fiend does not limit you to in-place changes like some hex editors.
- Work with huge files. Hex Fiend can handle as big a file as you're able to create, tested on files as large as 118 GB.
- Small footprint. Hex Fiend does not keep your files in memory. You won't dread launching or working with Hex Fiend even on low-RAM machines.
- Fast. Open a huge file, scroll around, copy and paste, all instantly. Find what you're looking for with fast searching.
- Binary diff. Hex Fiend can show the differences between files, taking into account insertions or deletions.
- Smart saving. Hex Fiend knows not to waste time overwriting the parts of your files that haven't changed, and never needs temporary disk space.
- Data inspector. Interpret data as integer or floating point, signed or unsigned, big or little endian...
- Embeddable! It's really easy to incorporate Hex Fiend's hex or data views into your app. Its BSD-style license won't burden you.
No programmer can survive long without a good hex editor, and Hex Fiend is the finest we've seen on any platform.
Privileged Helpers
MOAB hit in January 2007. Bill Gates (!) went on TDS to blather about how Apple's OS X was 'so insecure' and of course mention MOAB as well. All the while he was pimping his latest excuse for an operating system (at astronomical prices natch).
Did Apple feel offended? They should have ignored Gates. But they should not have ignored MOAB. But did things work out the other way around?
This alert can come up when running Hex Fiend.
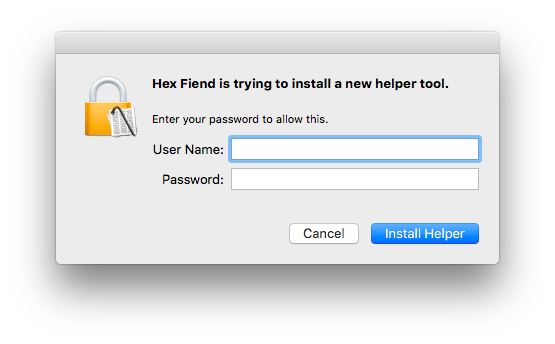
Naturally, as we have the only known tracking application for the platform, we ran it. And found this.
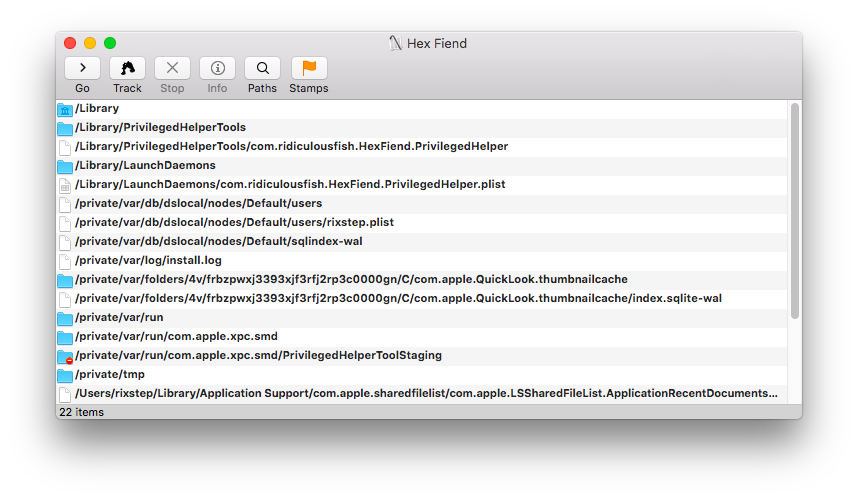
One key is in /Library/PrivilegedHelperTools. What Apple today want, instead of SUID, is their non-standard launchd starting your 'privileged' processes.
But this gets a bit dicey. Hex Fiend's com.ridiculousfish.HexFiend.PrivilegedHelper is marked 'root:wheel/0544'...
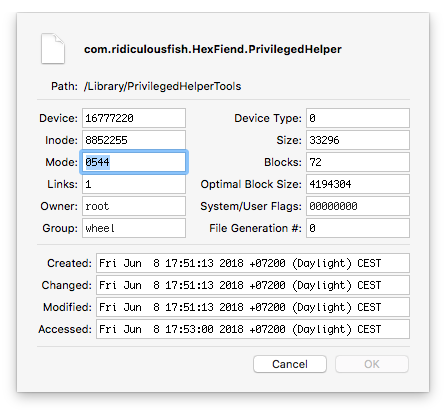
But how about its parent directory?
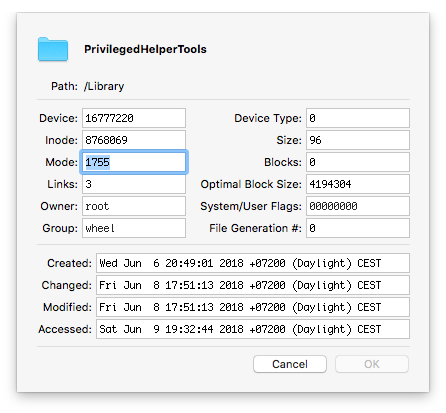
That's OK too, but how about its parent directory?
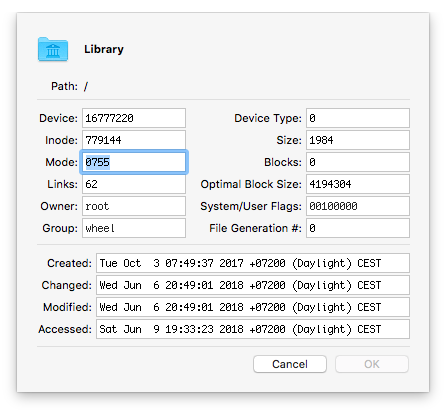
Note the 00100000 there for 'System/User Flags': that stands for:
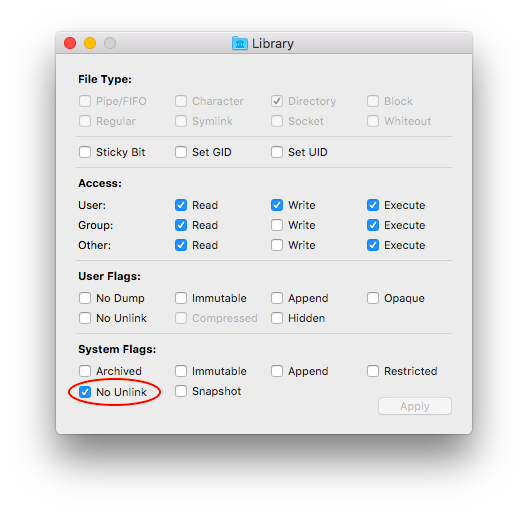
No Unlink. At system level. And you need root to remove it (the flag). Why? Because the whole house of cards collapses if com.ridiculousfish.HexFiend.PrivilegedHelper can be replaced, or PrivilegedHelperTools can be replaced, or /Library can be replaced.
[Previous OS versions used only the ACE group:everyone deny:delete. All this applies as well to /Library/LaunchDaemons. Ed.]
All the while Apple deliberately left the Opener hole open for years for the sake, it would seem, of third party software, and let Oompa Loompa happen. And so forth.
Don Yacktman also found security screwups in Apple's old Services menu. Servers running with root privileges and so forth. LMH found a barrel full in 2007 in /Applications. As is well known.
[The only major security screwups afflicting this platform have come from Apple 'architects' themselves. As a response to nonexistent threats from ISVs, Apple made the Services menu extremely difficult to interactively fine-tune. Ed.]
As there is - according to legend at least - elegance in simplicity, there might then also likely be confusion, chaos, and brutal attacks in the opposite, in what this platform's become today.
Something to think about.
'The Opener hole wasn't a hole - it was a crater.'
- Opener author
'OS X's implementation of AppleScript has a problem.'
- Charles Srstka
'A small but important minority of hackers devise exploits.'
- Apple
'Yacktman's book reads as if written by a single author because it was.'
- Amazon UK
See Also
AppKiDo
GitHub: AppKiDo Source
GitHub: Hex Fiend Source
Ridiculous Fish: Hex Fiend
Learning Curve: Rooting 10.5.4
Industry Watch: Get Root on 10.5.4
Red Hat Diaries: Proactive Mac Security
Developers Workshop: Hacking Code Sign
Apple Developer: Introduction to Secure Coding Guide
Tracker: Go ahead, have fun
Industry Watch: Opener 3.9
Industry Watch: The Story of Renepo
TechRepublic (Wayback): Apple: Opener's not a worm, trojan, or virus of any kind
Learning Curve: A Suggestion
Industry Watch: You're Root, Dude!
Industry Watch: You're Toast, Dude?
Learning Curve: The First Real Malware?
Industry Watch: ARDAgent: Here to Stay?
Learning Curve: Apple Redefine 'Epic FAIL'?
Hotspots: SLIPOC – Root Exploit of Mac OS X
Learning Curve: ARDAgent on Snow Leopard
The Technological: Walking into an Apple Store
Red Hat Diaries: Rooting Apple Can Be So Much Fun
Industry Watch: It's Not New It Starts with Ten-Dot-Two
Industry Watch: Huge, Crazy, Ridiculous OS X Security Hole
Apple Developer: AppleScript Overview
Apple Developer: Apple Events Programming Guide Hackers Handbook
Developers Workshop: Hackers Handbook I
Developers Workshop: Hackers Handbook II
Developers Workshop: Hackers Handbook III
Developers Workshop: Hackers Handbook IV
About RixstepStockholm/London-based Rixstep are a constellation of programmers and support staff from Radsoft Laboratories who tired of Windows vulnerabilities, Linux driver issues, and cursing x86 hardware all day long. Rixstep have many years of experience behind their efforts, with teaching and consulting credentials from the likes of British Aerospace, General Electric, Lockheed Martin, Lloyds TSB, SAAB Defence Systems, British Broadcasting Corporation, Barclays Bank, IBM, Microsoft, and Sony/Ericsson.
Rixstep and Radsoft products are or have been in use by Sweden's Royal Mail, Sony/Ericsson, the US Department of Defense, the offices of the US Supreme Court, the Government of Western Australia, the German Federal Police, Verizon Wireless, Los Alamos National Laboratory, Microsoft Corporation, the New York Times, Apple Inc, Oxford University, and hundreds of research institutes around the globe. See here.
All Content and Software Copyright © Rixstep. All Rights Reserved.
|