Home » Learning Curve
Windows: Give It Up, Dude!The BBC report on Conficker and this time they - gasp - mention Windows.
WORLD OF WINDOWS (Rixstep) -- The Conficker worm will be active again on 1 April, according to an analysis of its most recent variant by CA (Computer Associates).
'Win32/Conficker.C is a worm capable of blocking security related websites, terminating system security services, and downloading component files using time-based generated URLs', states the advisory.
No specific section of the advisory points out this only affects Windows systems even though it's painfully obvious to even the casual adept.
Even the BBC's Bill Thompson sticks his foot in it. 'Malicious software may just be a property of the network', states Thompson in the gaffe of the day. And then goes on to dance the BBC Sidestep again.
The CA Advisory
Even a cursory glance at the advisory should convince anyone Microsoft software is just not a good idea. Taking it byte by byte and between the lines builds up an absolutely horrific spectre - and provokes the recurring question why there isn't an outright worldwide ban on Microsoft products.
Method of Infection
You pick it up somewhere somehow but the advisory isn't saying. Considering the leaky nature of all Redmond products the candidate culprits are never far behind: Outlook, IE, things like that. Whatever: you get hit by simply hitting the power button. And then Conficker starts running. Woo-hoo.
When executed, Win32/Conficker.C drops a copy of itself using a random filename in the %System% directory. It may also drop copies of itself in the following directories:
%Program Files%\Windows NT
%Program Files%\Windows Media Player
%Program Files%\Internet Explorer
%Program Files%\Movie Maker
'%System%' is the most holy of holies on a Windows machine. It's the equivalent of Apple's /System/Library or any of the standard Unix directories such as /bin, /sbin, /usr/bin, and /usr/sbin. Now all you Apple OS X users and Ubuntu users and whatnot: try 'dropping' files in any of your Unix 'bin' directories. Go ahead. Have fun. And you Apple users: try 'dropping' files into /System/Library. See how far you get. Gee what a difference. Already.
In order to automatically execute [all the above 'droppings'] at each startup, it adds the registry entry below:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\ = 'rundll32.exe <worm executable>, <random string>'
'HKCU' is shorthand for 'HKEY_CURRENT_USER' which is a shortcut into a Windows Registry key. Please note how pathetically simple it is for malware to set system-wide startup items (at least for this user). 'rundll32.exe' is a Windows program capable of running DLLs (frameworks, shared libraries) as standalone programs.
It's mentioned elsewhere that these running programs are classified as services which is the next baddest thing to device drivers on Windows. Note again that getting such low level code to run required no privilege escalation whatsoever.
Additionally, Win32/Conficker.C checks for and tries to inject code into any processes executed with the commandline parameters 'svchost.exe -k NetworkService'.
So in other words Conficker is a virus too in addition to everything else. But a new form of virus: it doesn't parasite code on disk - it parasites code running in memory. The word 'process' is very important here and must be noticed: a process is not a disk file - it's a program loaded into memory.
Now normally on secure 32-bit systems the idea of one process so much as accessing the memory of another - much less writing to it - is folly. The whole idea of 32-bit security is that no process can in any way gain access to another.
This is an idea that holds on all operating systems on the planet - except for Microsoft Windows where it's but a whimsical theory. The operating system can't even let processes can access to virtual memory (backed up by physical RAM) that hasn't been thoroughly 'wiped' before use. But that's on other systems.
And 'svchost.exe' is one of these latter day 'improvements' (after Windows was already toasted to a cinder) whereby almost any rogue process can escape an egress firewall undetected.
Payload
Here's where things get very damning.
Modifies Registry / Lowers Security Settings
Win32/Conficker.C deletes the following registry entry to deactivate Windows Security Center notifications:
HKLM\Software\Microsoft\Windows\CurrentVersion\explorer\ShellServiceObjects\{FD6905CE-952F-41F1-9A6F-135D9C6622CC}
It deletes the registry entry below to prevent the operating system from starting in Safe Mode:
HKLM\SYSTEM\CurrentControlSet\Control\SafeBoot
Additionally, Win32/Conficker.C deletes the below registry entry to prevent Windows Defender from executing on system start:
HKLM\Software\Microsoft\Windows\CurrentVersion\Run\Windows Defender
'HKLM' is shorthand for 'HKEY_LOCAL_MACHINE' and represents a true 'root key' in the Windows Registry. It's also a key which always exists and always affects all users. Meaning the settings here as opposed to those above will affect all accounts on the computer.
And note (and shudder at) what's being done here with no privilege escalation.
- Turn off Microsoft's own 'Security Center'. No authentication necessary.
- Turns off the system's low level booting options. No authentication necessary.
- Turns off Microsoft's own ramshackle anti-spyware utilities. No authentication necessary.
You Unix/Linux/Mac OS X users: have you ever seen - have you ever heard of - a system where 'drive by' code on a web page or in an inbox can completely dismantle your entire system security architecture?
Deletes Restore Points
Conficker resets all system restore points and deletes any saved system restore points on the affected system.
This is getting ridiculous: all abilities to restore the 'system' from a previous state where it was (ahem) hopefully secure are wiped out. No authentication necessary. You Unix/Linux/Mac OS X users: can you imagine a system where a drive by attack wipes out all your backups?
Disables Services
Win32/Conficker.C looks for and disables the following services if running:
wscsvc - Security Center
WinDefend - Windows Defender (available in Vista)
wuauserv - Automatic Updates
BITS - Background Intelligent Transfer Service
ERSvc - Error Reporting Service
WerSvc - Windows Error Reporting Service (available in Vista)
- Automatic updates are turned off. This is a system option and yet no authentication was necessary to change it.
- Windows Defender gets clobbered again. What is being defended if the 'defender' can be turned off by a simple flick of a switch?
- Security Center is gone again. See above.
And so forth. Who designed this system? Ronald McDonald?
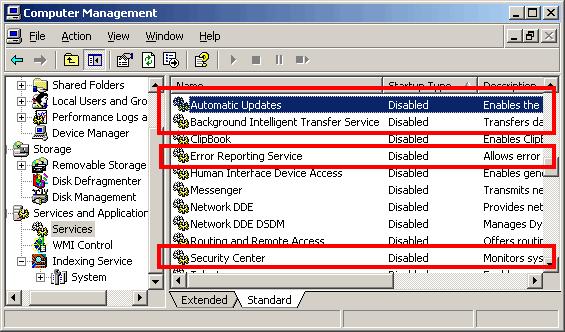
Microsoft security: all your defences turned off by a simple unauthenticated user process. |
There's more.
Terminates Processes
Win32/Conficker.C terminates the following security-related processes in an attempt to prevent its removal from the system:
autoruns, avenger, confick, downad, filemon, gmer, hotfix, kb890, kb958, kido, klwk, mbsa., mrt., mrtstub, ms08-06, procexp, procmon, regmon, scct_, sysclean, tcpview, unlocker, wireshark.
The above represent mostly third party anti-malware programs. Meaning no one is better at keeping you secure - they all get turned off by a flick of a switch.
Blocks Websites
Win32/Conficker.C hooks the following APIs to monitor and restrict access to security websites:
Query_Main
DnsQuery_W
DnsQuery_UTF8
DnsQuery_A
sendto
Note again this is system code that's being hooked willy-nilly with no protests from the operating system. And you have to laugh at what's going on with these calls even when benign: three types of DNS query and one of them for UTF-8? The other two for ASCII and for Microsoft 'wide' characters? Do those 'programmers' in Redmond think this is still the 1980s?
In its attempt to prevent access to security-related sites for information, help or software updates, the worm attempts to block running applications from accessing URLs containing any of the following strings:
avg., avp., bit9., ca., cert., gmer., kav., llnw., llnwd., msdn., msft., nai., sans., vet., agnitum, ahnlab, anti-, antivir, arcabit, avast, avgate, avira, bothunter, castlecops, ccollomb, centralcommand, clamav, comodo, computerassociates, conficker, cpsecure, cyber-ta, db networkassociates, defender, drweb, dslreports, emsisoft, esafe, eset, etrust, ewido, f-prot, f-secure, fortinet, free-av, freeav, gdata, grisoft, hackerwatch, hacksoft, hauri, ikarus, jotti, k7computing, kaspersky, malware, mcafee, microsoft, mirage, msftncsi, msmvps, mtc.sri, nod32, norman, norton, onecare, panda, pctools, prevx, ptsecurity, quickheal, removal, rising, rootkit, safety.live, securecomputing, secureworks, sophos, spamhaus, spyware, sunbelt, symantec, technet, threat, threatexpert, trendmicro, trojan, virscan, virus, wilderssecurity, windowsupdate.
It's probably at about this point you stop caring. Anybody dumb enough to run a system that can get routed this bad has it coming. But that's a fallacy: these idiots running this system are wreaking havoc on the rest of us and the Internet in general. In some way we have to knock them on their silly heads with a clue bat and get them to understand - and to leave those Microsoft products alone. So we move on.
Downloads and Executes Arbitrary Files
If the current system date is on or after 1 April 2009, the worm attempts to access pre-computed domain names to either download an updated copy of itself or download other malware. Below is a list of URL extensions used for pre-computed/generated URLs:
ac, ae, ag, am, as, at, be, bo, bz, ca, cd, ch, cl, cn, co.cr, co.id, co.il, co.ke, co.kr, co.nz, co.ug, co.uk, co.vi, co.za, com.ag, com.ai, com.ar, com.bo, com.br, com.bs, com.co, com.do, com.fj, com.gh, com.gl, com.gt, com.hn, com.jm, com.ki, com.lc, com.mt, com.mx, com.ng, com.ni, com.pa, com.pe, com.pr, com.pt, com.py, com.sv, com.tr, com.tt, com.tw, com.ua, com.uy, com.ve, cx, cz, dj, dk, dm, ec, es, fm, fr, gd, gr, gs, gy, hk, hn, ht, hu, ie, im, in, ir, is, kn, kz, la, lc, li, lu, lv, ly, md, me, mn, ms, mu, mw, my, nf, nl, no, pe, pk, pl, ps, ro, ru, sc, sg, sh, sk, su, tc, tj, tl, tn, to, tw, us, vc, vn.
CA couldn't figure out how to put those TLDs and stuff in readable alphabetical order. They needed help there. Tools like Unix sort are most likely still unavailable where they're coming from.
Additional Information
So that only one copy of itself runs at a time, Conficker creates a mutex in the format 'Global\%u-%u', where '%u' is a decimal number.
Well yeah DUH - mutexes (mutually exclusive synchronisation objects) are always used by malware. On Windows that is. Same thing actually.
The worm accesses the following websites to test Internet connectivity:
ask.com, baidu.com, facebook.com, google.com, imageshack.us, rapidshare.com, w3.org, yahoo.com.
Sir Tim will be happy to know his site is being put to good use.
Analysis by Zarestel Ferrer
BBC & Bill Thompson
Now it's the BBC's and Bill Thompson's turn. Of course the BBC made themselves outstanding the other day through Spencer Kelly who did the most unspeakable things in the name of Windows-centric journalism. But they're all in good company at the BBC. Now it's time for their Bill Thompson to wax philosophical on us.
Like many other malicious programs Conficker preys on Windows.
There will always be flaws and security holes in the rich, complex computing environment, and as a result there will always be space for malicious software to propagate.
Whatever happens with this particular worm, we have to hope that the security features in Windows 7 will reduce the impact of all types of malicious software in the Microsoft ecosystem.
But while it's easy to blame Microsoft for making its systems vulnerable we should also acknowledge that our own demands have contributed a great deal to the current situation and may make a complete solution unachievable.
Perhaps we should not be surprised that attempts to make these systems secure have failed.
I see a parallel between our attempts to have security and reliability in the complex computer systems we are building today and the attempts by philosophers at the turn of the 20th to reduce all of mathematics to formal logic.
Bill Thompson: the world always suspected you were a Bill Gates call girl. Now they know it to be true.
See Also
CA: Win32/Conficker.C
BBC Technology News: Holes in the Machine
|