Home » Learning Curve
Product Profile: XframePart of the ACP.
Start at the beginning. The lower right.
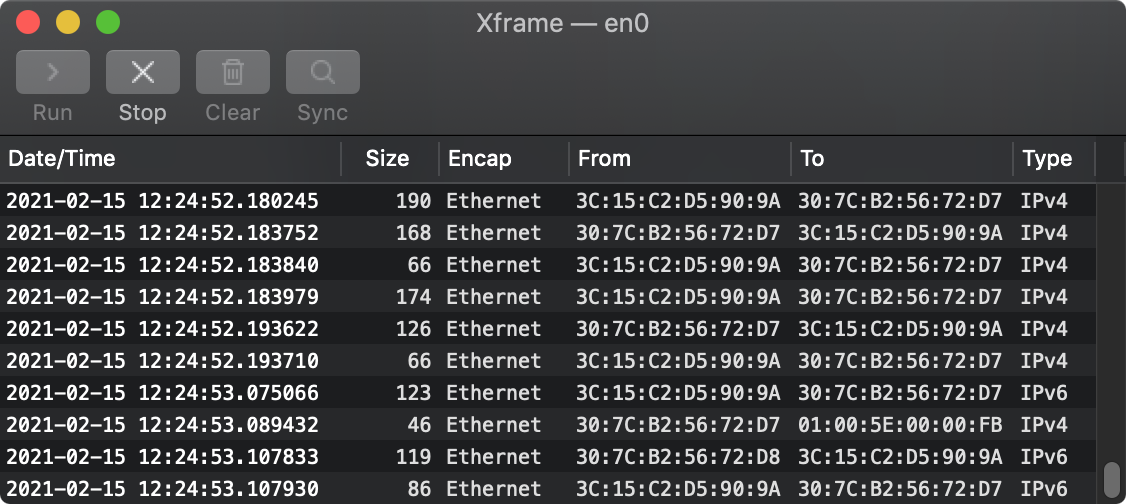
That's the main window of Xframe. That's where all the traffic comes in. Internet traffic is a matter of packets, chunks of data. Each packet comes with identifying headers that tell where it's supposed to go.
The granularity of the date/time is pretty good - down to millionths of a second. The packet size field is self-explanatory. The Encap ('encapsulation' or packaging method) is usually Ethernet, a Xerox invention. 'From' and 'to' are local hardware addresses. The 'type' field says where to go next.
Normally one thinks in terms of enclosing data through the various communication layers to send out. This is the opposite. Xframe 'sniffs' the line, sees what's there, and shows you what it finds.
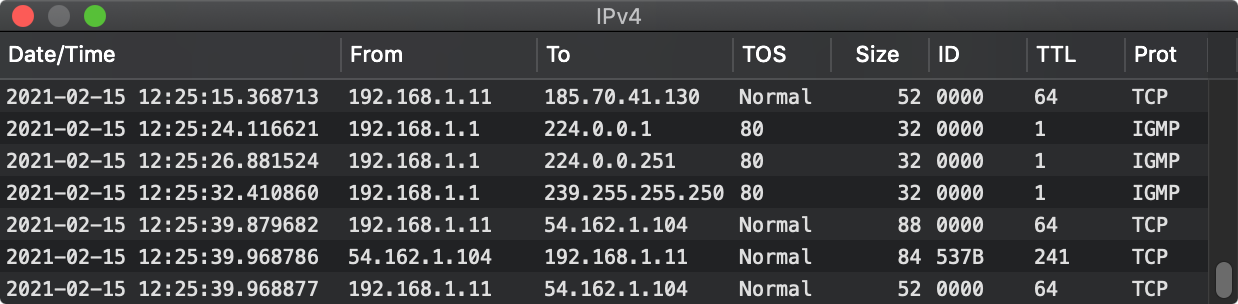
The first image above sees the type 'IPv4' which is Internet Protocol version 4. When Xframe sees that type, it furthers the packet to the IPv4 window.
The date/time field is the same. The 'from' and 'to' fields are now actual Internet addresses. The 'TOS' field is 'terms of service'. The 'ID' field is an internal identifier. The 'TTL' is time to live, or the number of hops between servers that can be used before the packet expires and isn't sent on anymore. The 'prot' field indicates how this rather 'raw' packet is to be further interpreted - as, for example, TCP or IGMP in the above example.
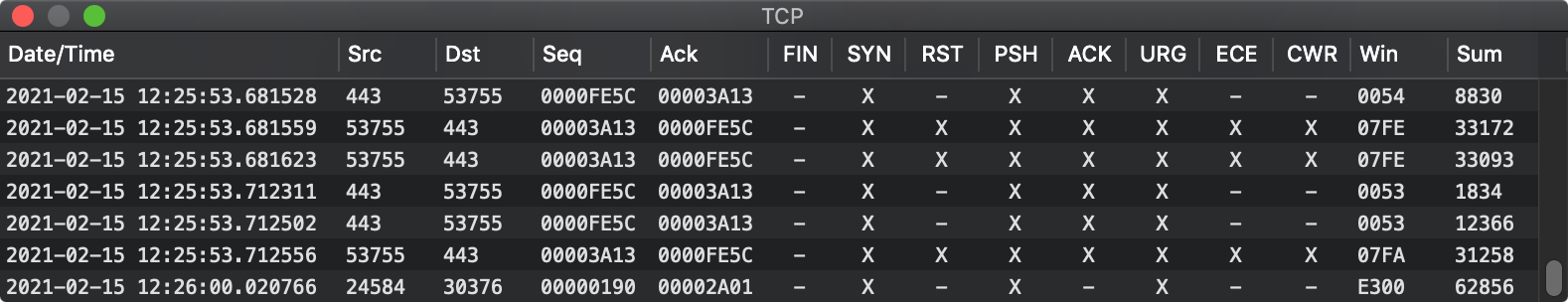
The TCP window - Transmission Control Protocol is one possible destination for a packet that ends up with IPv4. Internet traffic is 'divided' as it were into two levels: the simpler 'IP' of which there are currently two versions and the overseeing TCP which, as its name connotes, controls what's going on.
The date/time are again the same and correspond to the same field data found in the earlier images. The Src and Dst fields are for the ports the packet is routed between. The Seq ('sequence') and Ack ('acknowledge') fields help thread the packet into the series to which it belongs.
The FIN, SYN, RST, PSH, ACK, URG, ECE, and CWR are flags used to govern the transmission. TCP connections begin by sending a packet with the SYN flag, getting back a packet with the ACK and SYN flags, and finally sending back a packet with the ACK flag - the 'TCP handshake' that establishes a connection with a remote server.
The Win field indicates how much data the sender will accept from the remote server. The Sum field is a checksum for the packet. The Urp field, the 'urgent pointer', is used if the URG flag is set.
The above is the usual route for Internet connections. Today IPv6 ('Internet Protocol version 6') is superseding version 4 to afford more address space (more computers on the Internet).
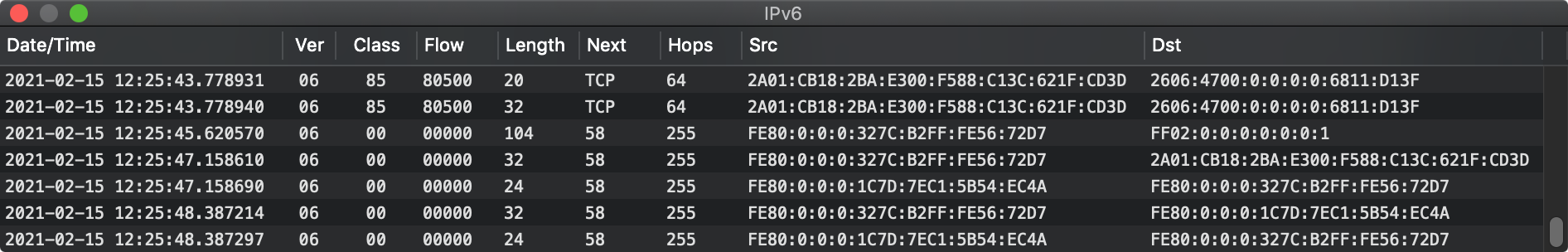
There are other routes a packet can take. ARP ('Address Resolution Protocol') is one.
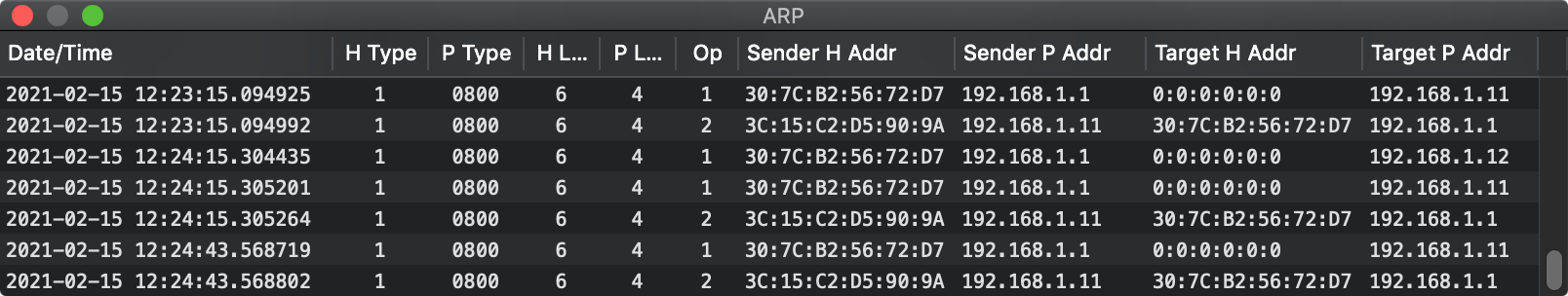
Packets can be inspected. A double-click on any row of any Xframe window summons up the contents of the packet in question, with offsets given in 128-bit hex.
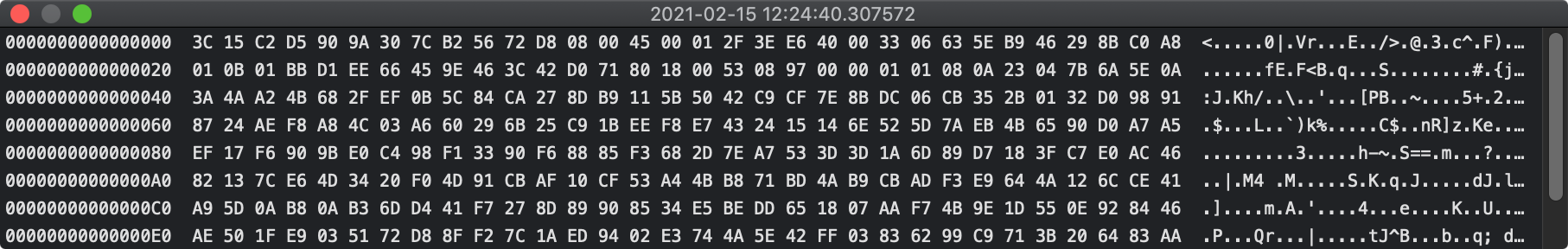
All of the above can be logged to disk as well.
2021-02-15 01:28:00.096510 74 Ethernet 30:7C:B2:56:72:D8 30:35:AD:DE:C5:9C IPv6
IPv6
2021-02-20 01:28:00.096510 06 4C 40600 20 TCP 57 2606:4700:0:0:0:0:6811:D23F 2A01:CB18:2BA:E300:D9C7:D408:1A83:C6F2
TCP
2021-02-20 01:28:00.096510 24588 25676 00000014 00002606 - X X - - X - - 0000 0 0
Xframe for OS X was created several months after the corresponding application for Windows, the design for which was based on that used for a realtime debugging tool. The idea - of having sovereign windows communicating with one another - was rather radical for Windows. Once the design was complete, the programming took but one day where every milestone was chalked out, down to what was needed before the morning coffee break, the break for lunch, and so forth.
Programming for OS X followed the same path but needed to be repeated each time Apple ripped apart and reassembled their system infrastructure.
It's the main window that gets the traffic and starts the 'demultiplexing', propagating the packet information 'upward'.
See Also
Xframe: Packet Sniffer
About RixstepStockholm/London-based Rixstep are a constellation of programmers and support staff from Radsoft Laboratories who tired of Windows vulnerabilities, Linux driver issues, and cursing x86 hardware all day long. Rixstep have many years of experience behind their efforts, with teaching and consulting credentials from the likes of British Aerospace, General Electric, Lockheed Martin, Lloyds TSB, SAAB Defence Systems, British Broadcasting Corporation, Barclays Bank, IBM, Microsoft, and Sony/Ericsson.
Rixstep and Radsoft products are or have been in use by Sweden's Royal Mail, Sony/Ericsson, the US Department of Defense, the offices of the US Supreme Court, the Government of Western Australia, the German Federal Police, Verizon Wireless, Los Alamos National Laboratory, Microsoft Corporation, the New York Times, Apple Inc, Oxford University, and hundreds of research institutes around the globe. See here.
All Content and Software Copyright © Rixstep. All Rights Reserved.
|